[3MAR2016 Note: A much newer, better method has been developed and is documented in this post.] A common question among commenters to this blog when I write about my Stratasys FDM 1600 is “how did you hack the cartridge?” Newer Stratasys machines such as the Dimension series (P-Class machines – I assume named after the […]
[3MAR2016 Note: A much newer, better method has been developed and is documented in this post.]
A common question among commenters to this blog when I write about my Stratasys FDM 1600 is “how did you hack the cartridge?” Newer Stratasys machines such as the Dimension series (P-Class machines – I assume named after the Prodigy, which I think was the first Stratasys machine to use cartridges) don’t have plain old wire welding type spools like the old FDM series – instead, they have the filament stored in a large cassette. This is nice as it keeps the filament dry without having to keep it in a dry box and it makes loading in new material (or swapping colors) a breeze. On the down side (as many Stratasys owners have apparently discovered), Stratasys went the route of inkjet printer manufacturers and have ‘chipped’ their cartridges so that you can’t simply refill the cartridge with material and continue on. While this isn’t a hindrance to me and my old machine, I’ve still been curious to know if there’s a way around this (if I ever come across a Dimension for cheap, I’ll need a way to feed it as well). Note: I understand the big T-class machines (named after the Titan model, I assume) still use large spools, though I believe the spools also have a chip module (but hey, if you can afford to buy a T-class, the consumables cost probably isn’t a big concern).
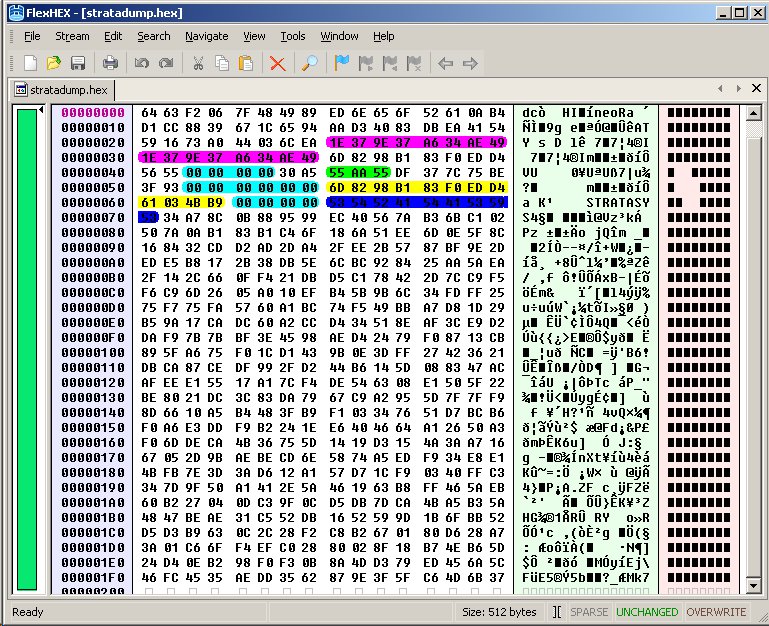
Inside each Stratasys cartridge is a Maxim DS2433 one-wire EEPROM (in a SO-8 package) that the machine communicates with. This is a simple 4kb (that’s kilobits – only 512 bytes of storage) device, and reading/writing them is reasonably straightforward – a library most likely exists for 1-wire communication no matter what your microcontroller of choice is (Arduino enthusiasts, look here). Dumping the contents of one yields hexadecimal gibberish, unfortunately. What’s more, you can’t simply clone one of them, as each has a unique 48-bit serial number lasered onto the die at the time of production, and this serial (presumably) is used as the seed to encrypt/obfuscate the EEPROM data. This has been enough to dissuade most tinkerers from playing further with the system, though Bolson Materials may very well have cracked the code, as they are able to provide new EEPROMs with their cartridge refill spools.
Thanks to some hacking by the shadowy figure known as ‘Dervish’, it’s been found that only a small portion (12 bytes) of the EEPROM is dedicated to storing how much material is left on the spool. As a cartridge was used, the EEPROM was read out at various points and only bytes 0x58-0x63 changed over the life of a cartridge. Specifically, here’s the layout of data on the EEPROM as known thus far as a result of reading EEPROMs from several brand new cartridges:
0x00-0x41: scrambled data (commenter lgg2 noted that 0x28-0x2F is identical to 0x30-0x37, highlighted in purple)
0x42-0x45: 0x00000000
0x46-0x47: scrambled data
0x48-0x4A: 0x55AA55 (highlighted in green)
0x4B-0x4D: scrambled data
0x4E-0x4F: 0x71BE, 0x72BE, 0x73BE, 0x74BE, or 0x75BE
0x50-0x51: scrambled data
0x52-0x57: 0x000000000000
0x58-0x63: filament remaining (scrambled data, highlighted in yellow) – on an unused spool, 0x62-0x63 is always 0x4BB9, but this gets modified (along with 0x58-0x61) as the cartridge is used. Perhaps 0x62-0x63 is an unencrypted checksum?
0x64-0x67: 0x00000000
0x68-0x70: 0x535452415441535953 (‘STRATASYS’ in ASCII, highlighted in dark blue)
0x71-0x1FF: scrambled data
Simple enough, right? Just read in the EEPROM at 100% full, respool it with generic material when empty and write the 100% full data back to the EEPROM… Well, not quite. You can certainly use this respooled cartridge in a different machine, but not in the same one, as they remember what cartridges they’ve already used (that serial number on the EEPROM). This is where Dervish tore into the guts of the machine and began the really clever hacking. When you open up the side panel of a Dimension, here’s what you see (image taken from Brad Rigdon’s Print To 3D gallery):
Brad also has a nice video on youtube that shows the full workings of the machine. The electronics appear to be composed of 3 boards – the large PDB (Power Distribution Board) on the left, the SBC (Single Board Computer, just a PC) in the center right above the hard drive, and what appears to be a motion controller board (in the upper right, connected to the SBC via a 16-bit PC/104 header). As per the troubleshooting section of the Dimension/SST Service Guide, the motion controller board in the upper right is known as the ‘186 board’. The SBC pictured appears to be an Ampro P5v, though some Dimensions use a Nova-600. After connecting a keyboard and monitor to the SBC, Dervish found that the computer is running Linux (Red Hat 8, specifically – not Fedora 8, but the circa 2002 version with a 2.4.x kernel).
By rebooting the system he was able to enter single user mode (at the LILO prompt, enter ‘linux single’) and could change the root password to whatever was desired (type ‘passwd’ at the prompt, enter a new password, then enter again to confirm). After rebooting once more into standard mode as root with his newly minted password, he modified /etc/sysconfig/iptables to open up port 22 so that he could ssh into the system and hack remotely without having to be at the console itself (the sshd daemon does not run by default, so adding the line ‘/etc/init.d/sshd start’ to /etc/rc.local is also required). While he had been able to modify temperatures on the machine by using Stratasys’s ‘Maraca’ software (the CatalystEX software offers no ability to tweak the system), direct access to the SBC allows much greater control over process parameters such as adjusting rollback. All the configurations are stored within the /mariner/config tree (the hard drive image covers multiple models), and it can be tricky to determine which ‘gender’ (kona, lanai, spinnaker, oahu etc.) corresponds to a given machine, but noting which directory has the most recent modification date is a dead giveaway.
The holy grail turned out to be the discovery of an innocuous sounding file named ‘system.dat’ located in the root directory. This is where the Dimension apparently stores a list (in binary) of all the cartridge EEPROM serial numbers that it has seen before. Delete this file and the machine gets amnesia, allowing respooled cartridges (with the EEPROM rewritten to show 100% full) to be used again. I assume creating a cron job to delete this file periodically (or using rc.local to delete it on startup) would also work.
As far as I know, this constitutes the cutting edge of Stratasys hacking – I’ve heard rumors before of people having bypassed the cartridge EEPROMs, but this is the first concrete information I’ve seen on how to accomplish it. If anyone has further information, please leave a comment!

Very good info.
Thanks.
Another curiosity,
In the offsets 0x28-0x2F // 0x30-0x37 had the same bytes.
Excellent find – I can confirm that this appears to be the case, and I updated the overview.
Hi, i’m having Curling Part problems on my dimension elite, and i’m looking for Maraca Software. Have an idea ? Could not find it on the web and you seems to know a lot about FDM.
Thanks, Franck (frenchie)
Franck –
This guide has some suggestions on reducing curling and other issues: http://www.aetlabs.com/files/downloads/Part%20Qlty%20TS%20Guide.pdf
Bonjour, moi aussi j’aimerais bien réussir à utiliser du fil d’ABS moins cher que ce que vendent les revendeurs de STRATASYS car c’est un sérieux frein pour imprimer des objets.
J’ai vu que tu es français et c’est plus facile pour moi qu’en anglais.
Si tu as des infos à me communiquer, je t’en serasi très reconnaissant.
Merci
Hello!
This hack work fine only with old printer models.
The new one – stratasys uprintplus has another cartrige.
It consists of protected eeprom with SHA-1and limit switch. (family code B3h – (maybe like ds2432 – 33h ?))
Eeprom has secret code, and printer send data with encryption.
I can read rom memory and find 12 “wonderful” bytes on full chip, (for used chip consist of 16 bytes)
but i can’t rewrite this data to empty chip without secret code …. (
now i try to logging communication protocol and analyze it… hope it helps
Very interesting! I suppose this may be in response to Bolson supposedly cracking the code for the Dimension cartridges. I wonder if they’re using the same secret across all cartridges? I can’t find any mention of a 0xB3 family code for 1-wire devices – does the EEPROM have any markings on it?
From reading the abbreviated datasheet on the DS2432 (the full datasheet is apparently confidential, but this might be it: http://www.ibutton.ru/pdf/Dallas_Sem/1-Wire/DS2432.pdf), you can supply a new secret to the chip without knowing the old one, but if the printer is still trying to use the old one, writes aren’t going to work (and since Stratasys started verifying writes to the EEPROM at some point, it will probably flag the cartridge as bad). Sure, you can sniff the communications and find the MAC for a given write command, but then you’d have to brute-force the SHA-1 hash (good luck with that).
Seems the best way to get around this would be to build an EEPROM simulator that the printer can talk to – if the simulator accepts any MAC provided, it should be able to fool the printer.
Very interesting post!
Certainly makes me glad I’ve got a ‘1650 that didn’t have a chip….
—-John
Hello!
There is no marking on chip. It looks like piece of Si with epoxy resin around it.
May be it is DS28E10 ( http://www.maxim-ic.com/datasheet/index.mvp/id/6577 ) . I cant find full datasheet with family number.
The problem is – MAC calculated using a) secret code and b) data to write. So I couldn’t get chip back to 100% only to 99%, if sniff this write sequence.
there are two ways
1) if secret is constant – sniff first write sequence and use it in future for this chip.
2) if secret may change (ds2432 allows that), it’s a problem, may be we need disassemble software part.
interesting facts
– i cant simply change eeprom to the another one (without write protection), printer constantly check authentication.
– if i remove chip from working printer it continue his work but stay on pause after each layer of model. after reboot and connecting the chip back printer display original chip state.
Building the full emulator is not so easy as reader/writer and I don’t know would printer check written data.
If you have any used EEPROMs, you could try decapsulating them like Flylogic does (http://www.flylogic.net/blog/?category_name=device-teardowns) and have a look at the die under a microscope to see if you can find a munufacturer name or part number.
As an owner of dimension 3d printer, that works on stratasys system, I am very interested in discovery you made. At this point I would like to ask, if this also works on dimension bst 768 printer.
With best regards Jernej
Yes, this technique works on the BST 768.
I owe Dervish some beer (a lot of beer!). hooking up the vga and keyboard was not a practical option on my 768 (headers,no connectors). i just pulled the hard drive and mounted it on a ubuntu linux box and turned on ssh by doing some editing.. from there, followed the lead on killing the system.dat file on bootup…
genius!!!!!!!
works perfect
thanks to my genius friend TOM (who is definately getting a case of dogfish head 60 minute IPA)..
JJ — off to print!
Thank you for the answer, I really appreciate it.
Jernej
My report about analyzing chip’s protocol with SHA1 :
Chip has family code B3h, but seems fully compatible with ds2433 (33h) commands system.
Authorization packet consists of write buffer command, read memory command, calculation MAC command.
MAC calculated using a+b+c
a) data stored in memory
b) data stored in buffer
c) secret code
So I know MAC result, a), b), and i don’t know c).
The bad news – 8 bytes unknown data is very bad.
I wrote simple program calculating SHA1 hash – 6000 hash/s (athlon 1500MHz)
Commercial avaible cuda GPU bruteforcer – 100M hash/s
Possibility of FPGA bruteforcer 1-10G hash/s
All these cases are too slow.
Maybe it is possible to use electrical sharp tip directly inside the chip and to measure out voltage of secret code trigger’s. But i haven’t such qualification and such equipment.
the good news – current version of program has minor bug, and it allows us using the same chips.
Fantastic information, thanks! I agree, brute forcing the hash isn’t practical at this time, especially when there are weaker areas to investigate for the MAC.
Anyone know where I can get hold of a copy of the Maraca software?
i have maraca if u still need it
Henry in CA
hfletcher@gaugemate.com
I do still need it. Sent you an email.
Hello, Arduino Enthusiast here,
Would someone please help me or point me in the right direction to figure out how to read the hex values of the chip. I have an arduino, a 4.7k resistor, a multimeter and the small GF201 switch with the eeprom on it. THough I have all of this, I cannot figure out which pins to connect to, or what code I should be using in the arudino IDE. Any help would be much appreciated
Use the 1wire Library and ther are sone sample progs there — start with something like a DS18B20 temp sensor to get going…
Did you notice that on new spools offsets 0x38-0x3F // 0x58-0x5F are the same???
0x40-0x41 // 0x60-0x61 could be checksums or something
I didn’t notice that – excellent catch! I think it’s safe to assume that 0x38-0x3F contains the original amount of material on the spool. I’ll have to update the post when I get a chance.
And 0×4E-0×4F I think are related to manufacture date of production (week), and I’m figuring it out how to calculate them
Actually, I think 0x28-0x2F and 0×30-0×37 are the manufacturing and first use dates. I noticed in a log file from a machine that these two values were identical when read – apparently Stratasys doesn’t update the ‘initial use’ field in the EEPROM.
Can you drop me a line?, I would like to check some topics on EEPROM readings
Sent you an email – post here again if you didn’t get it.
How can one read/write to EEPROM ds2433 chip using arduino?
Does anybody have a code that we can use?
Thank you!!
Hey Blue, sorry but I’ve been away on vacation. I am writting you a mail tomorrow. Cheers!
Hello,
Is it possible to contact ‘Dervish’ cause at the moment we are connecting a keyboard to a dimension 3D printer, and maybe he could provide some help for us.
Greetings
I haven’t heard from Dervish in a while, but connecting the keyboard and monitor isn’t hard – you just need the correct cable set from the maker of the SBC.
Hello Blue
I am have a FDM2000 but no software.
Where can i get the sotware to run this machine.
Stratasys no longer supports this model
Any help would be great
Thank you
Marcio
I’ve got four questions.
1) Is there someone who can send me the maraca software
2) Does anybody can show me, with print screens, how to open port 22?
3) How can you modify the temperature of the heating head?
4) Where can I modify the distance between the support and model heating heads?
Greetings,
Jeroen
I have a stratasys prodigy plus, and while fooling around in the Linux system, accidentally overwrote a file called lcdcmds. I was wondering if anyone on this blog could get another copy for me? It doesn’t seem to be stored anywhere else! 🙁
Do you have a firmware package that you can re-upload? That’s probably the best way to fix it, as that file may get changed as new firmware versions are released.
I would like to reload the chip on a stratasys spool to reuse the material left on the spool. I am using an arduino uno with a maxim ds2433 eeprom to read/write the .hex file in an attempt to reload the chip. Any advice on the code to make this happen?
I’m tempted to try this on my printer at work… just got a 1200es. is there a way to SSH into the SBC without having to remove it? I noticed a com port in the back of the printer.
Nevermind – just noticed the answer
Hi guys, i have the Stratasys Fortus 250mc and i’m trying to refill the spool. I see that most of you doesn’t have the right tool to read/write the 1wire eeprom… well you can buy for cheap the buspirate from http://dangerousprototypes.com . It will let you do anything you want on some serial bus (usart, spi, i2c) 1-wire included. I’m using it and it works great, you just need to write a sw interface to fill the addresses with your data.
My problem is that i found inside /mariner/config/ the system.dat file, but even if i remove it, the machine regenerate the file and doesn’t accept the spool with the reloaded dump (give “material error…”). do you have any idea?? Fla
The system.dat file to delete is the on in the root directory, not anything in /mariner/config. [edit] I stand corrected – I wasn’t aware that it appears in /mariner/config in newer firmware versions.
I want to refill some cartridges for a BST 768.
Do I have to dump the EEPROM when the cartridge is new? Can I find a way to refill all the old cartridges which don’t have virgin EEPROM dumps?
Flavio, could you provide any further information on using the BusPirate with the 1wire eeproms?
Correct, you need to get an EEPROM dump before you start using a new cartridge. There is no way to refill a cartridge chip unless you read out the EEPROM when new (unless you work for Stratasys and have access to the program that generates the EEPROM data).
I have access to more than a few empty cartridges, would it help if I could produce a dump for each of them? If anyone is interested in that data, let me know.
Can someone point me to a good resource for reading/writing these EEPROMs with an Arduino or BusPirate? I googled a bit but failed to find anything good.
Empty cartridge dumps won’t be of much help, but full ones might. I’ve read out the EEPROMs with a Bus Pirate, but it required cutting the trace on the EEPROM board for the resistor. I still need to try using a 12v power source, as I think that’s the trick to getting a read.
Have Blue, could you detail where to cut the trace / use a 12V power source? I was under the impression one simply had to connect the ground (to pin 3), and a 4.7k ohm resistor between data and pin 4.
Dan, I’m actually hoping to do a blog post on reading an EEPROM with a BusPirate. The problem with the Stratasys EEPROM board is that the resistor in place is a 4.7k pullDOWN and not a pullup. I think this is why 12v is required.
You don’t need to cut the trace to read a cartidge with bus pirate. Connect the bus pirate to trace closest to hole to GND and other trace connect to MOSI. Connect the bus pirate to the computer USB. Start a terminal program (I used Realterm) and connect to COM for bus pirate (mine was COM2) @ 11520 buad, no parity, 6 data bits, & 1 stop bit.
In the open terminal window:
1) Type ‘m’ for menu.
2) Type ‘2’ for 1-Wire.
3) Type ‘w’ for power supply.
4) Type ‘P’ for pull-up resistor.
5) Type ‘[‘ for bus reset.
6) Type ‘240’ for search.
7) Type ‘204’ for skip ROM function.
8) Type ‘(0x55)(1) 0xf0 0x00 0x00 r:512’ for dump.
Save the dumped data from the terminal window.
Well, there you go! Thanks, John – I was concerned that the resistor would mess with getting a good read with the Bus Pirate. I’ll have to give it a try myself.
Is there any Progress on this? I’m also trying to get a read from it with an Arduino but it won’t work.
Is it even possible with an Arduino or do I Need to get a Bus Pirate? I don’t want to cut a trace or anything non reversable because I’m trying to build a deviece to simple scan the chip and write it back later.
Hello I have a Dimension Elite, and during the operation the power was cutted. The machine starts but the display didn´t show anything. I do the Cycling Power procedure but, the machine don´t power off. Some can help me with problem?
Sounds like you may have some filesystem corruption – best to hook up a keyboard and monitor to see what bootup messages there are.
Thank you, yesterday we connect a Keyboard and monitor and we saw that one of the file it´s damage. To repair this file I need a password, to enter into the repair console, but I don´t have one. Do you which can be password or where can I find it?
Best Regards
Emiliano
If it’s asking for the root password, there is no valid root password by default – you’ll need to boot the machine into single user mode and create a valid password.
Hey there
I have a BST, which doesn’t get past boot up stage, I am wondering if I may be able to have a direct copy of the firmware data? it passes the HD testing stage, requires a password ( to which it says incorrect, and says expected 1×72344 (or something, i cannot remember the numbers) found FxFFFFF
Im a little clueless 😀 so any help would be very gratefully received! Thanks
I wonder if you’re having the same difficulty as Emiliano above… Can you boot into single user mode and set a root password?
Maybe! i can login as single and change the root password however i am still coming up against the same problems which says
Master login : DPM: Invalid signature: Expected 53595353 got ffffffff
DPM : Failed to aquire 28 byte I/O memory range at 0xd1000
DPM : revision 1 controller with memory size of 8188 bytes
DPM : revision 1 little endian controller with a 8188 byte dual port memory
I know the hard drive is on its way out (noisy!), and have tried to get a ghost image of it before it dies with little success as it skips some partitions saying they are damaged. could this be the problem? Thanks!
Ah, that error seems to indicate difficulty with communicating with the controller board. It’s possible that hard drive corruption could be causing the issue, but it’s hard to say. I’ve used SpinRite (http://www.grc.com/sr/spinrite.htm) before to recover/repair bad sectors – might be worth a try.
As you can see, the bytes from $0038 to $003F are same than $0058 to $005F, where the spool material left lives. Can you tell me the name of the cartridge where you do this dump?. Usually, the cartridge has the follow names: P401_GRY or similar (depending the material features and color). I’m sure the cartridfe name’s is inside this bytes (between $0058 and $005F).
Best regards.
I don’t know what specific material code that dump would have read out, though I think it was probably just ‘P400’. For various reasons, I really don’t think that specific string is encoded on the EEPROM – I’m sure it’s just a numeric identifier which corresponds to ‘P400’, ‘PC_ABS’, ‘P430_NAT’, etc.
i am not an expert. But do you guys know if i put diode on the eeprom which is 100% so machine can’t write on eeprom.
Does it make sence?
I understand what you’re suggesting, but it won’t work – since the EEPROM is a 1-wire unit, there is no write protect pin or any other line that can be toyed with. Since there’s only a single pin for input data, output data, and parasitic power supply, anything that affects writing will also affect reading.
Dear have blue
Im Daniel, from Buenos Aires Argentina.
I have read your explanation and was enjoy it, English isnt my lenguage, but I understood in genral.
I dont know nothing about electronic, but I looking for about haked a uprint material chip , and you give me a good information about Bloson material.
I by pass the security equipment, and could used a genric material in the machin, but I couls made this in the mechanical way .
The proces its not complicate, you need put a original spool and when the equipment pull the material in, you must disconect the house and at the same time introduce by the house the generic material, when the generic material arrived to the extruder the original one stop and the machine pull for the genric one, during the construction proces the counting stop , you preserve the total live of the original spool and chip but used the generic one.
I whish you could understand my primitive english.
By
Daniel I am very interested in understanding more abbout what you did. Are we talking about the old spool that came incased? Hoy did yuo manage to introduce the material in the house??
Dear Monko
i have the Uprint model, its a small one, on the back have two hose, one for the material and other for the support, in other models the hoses are inside the equipment.
The steps are the following.
Firts, discharge the material
Secomd disconect the material hose, and introduce the generic material in the machine , but stop before arrived into the extruder.
Introduce the original material cartridge in the machine and charge it, the filament will into the machine and go out ( becouse you desconected the hose).
When the material go out you must push the generic material into the machine until will be catch for the extruder motor, at this moment the original material stop, becouse the extruder motor take que control and pull the material, but are pulling the generic one,
Conclusion, all the time you used the generic material an d not the original , and because the counting mechanism work when the original material run, the chip didnt change in the charge percent.
So sorry for my dab explanation, if you need I could take some pictures for you.
Daiel
Sorry, one detaill, the generic material must be introduce in the machine by the hose, like if the original material continue through the hose.
Daniel –
When does the printer actually write back to the EEPROM? Is there an encoder on the uPrint that monitors how much filament has been fed out of the cartridge itself?
I really dont know which is the eeprom, I guess understand your question and I try to response.
I used this process every time when the spool chip have only 1 or 2% , and I could print practicaly one generic spool whith 1 or 2% .
Im not understand very well the electronic mechanism and in particular what do the machine to count the filament, but probing i could by pass this counting.
If you whised ask me other think please dont hesitate.
Daniel
Assuming the guts are at the rear of the machine, does the entire metal case need to be removed to get to it? Once open and I get SSH working, how do I then connect?
I need to calibrate the table/head distance so will be hunting for a config or knowing my luck it will be in binary
thanks
The guts are at the rear – you’ll need to use appropriate keyboard and monitor adapter cables to get into single user mode. It’s just a panel that you’ll need to open – should be easy to access the SBC. Once you have SSH running, you can connect directly over the network – no further need for the monitor and keyboard.
Does anybody know of the current, new, Stratasys cartridges can still be hacked as described in this post? Is it the same EEPROM being used?
Also, thought on disconnecting the spool sensor with the new cartridge, such that the amount of material remaining is never decreased, and it can be continually reloaded?
I have lots of Model Material which is showing 0%. Let me know if any one is interested.
I would be happy if some one can use them.
My coordinates are
43.754227,-79.632016
I’ve not confirmed chip swap actually works on my Uprint ESplus- but would be happy to swap a chip to test it with you. If it works I too have several 0’ed chips– we could swap all. what machine do you have?
write me at MrGreatRakes@Gmail.com
Daniel- you are a genius. The mechanical hack worked on my Uprint ESplus.
So all you folks who are reprogramming your code – which i don’t understand- if you pull the hose off the back and jam in the generic filament it sucks it in- but does not remove % from the chip. Done. sounds crazy but works.
I’ve been running a test- I pulled out a spool and put new filament in the cartridge- but with the original chip. i started the loading process. when the new filament came out of the hose i pushed the original filament manually into the now open hole till it was recognized and the pulled in from the head by the motor. My part has been building but the chip has NOT been counting down. its weird because you have to have an extra spool on the outside of the machine, and i have no idea what in cartridge would make it count down… but apparently if the filament isn’t moving thru the cartridge it doesn’t count down.
Now i can get material from other places!! 4 spools for the price of one from SYS. Glow in the Dark her i come.
drat. spoke too soon. too good to be true. my % is going down— but seems slower. i’ll update.
Any update? Does it work?
and in return…. my hack.
You can reuse the trays about a million times.
After each use- scrape flat.
Fold a paper towel into a flat pad. dip it in Acetone and give it a series of quick wipes. The tray will look shiny but parts will stick great. In fact i was having trouble with my factory trays when i was being meticulous and buying new ones. Now i am abusive- a quick wipe of Acetone and boom, never a peeling part.
For the record, I tried imaging the hard drive for my Uprint ES plus, running the machine and then re-imaging as discussed way above- It did NOT reset the clock for the chip. Perhaps they’ve upgraded the chip to write as well. the chips on these spools have 4 contacts.
Any similar experiences?
The EEPROMs have always been written to – this is what allowed you to swap between different color cartridges (even between different machines), yet retain an accurate count of how much material was left.
Hi, I’m a student at a high school and am very privileged to have a 3-d 1200es printer at my school. Though due to the high cost of printer cartridges from dimension, we aren’t allowed to use it (much). If we were able to use material from companies like Makerbot, we would be allowed and probably be encouraged to use the printer. We have a few empty cartridges lying around with chips in them and I also have a Arduino. Although i haven’t programed anything with 1-wire communication. The main issue is that since it is a school printer, I’m not allowed to take apart the printer because of insurance. I am allowed to mess with a cartridge and do whatever i want with them, plus i’m allowed to reset the printer. Plus with a set plan i might be able to convince my teacher to let me have a go at erasing the serial numbers on the printer as long as i can do it from a remote computer.
Any and all help would be appreciated. Send me a email @ justinhockey@gmail.com
Wow, a 1200es – you are indeed privileged! I’m really disappointed that your school limits your access to the machine just because the materials are pricey – the 1200es is probably a good $35k-$40k machine, so that’s a bit like saying “no, you can’t drive the Ferrari because premium unleaded is so expensive”.
If I were in your position, I’d suggest to the powers-that-be that the school sell off the 1200es and get a bunch of Makerbots instead. Heck, the yearly maintenance fee that Stratasys is charging your school for the 1200es would cover a Replicator by itself, and then you’d be able to run PA-747 filament all day long from a variety of sources. This is actually what Frankie did for UWM’s Digital Craft Research Lab – we had been hoping to get a used old model Stratasys for several thousand dollars, but Frankie wound up building a fleet of RepRaps for the same price instead. You may not be able to provide every student in a class with their own machine, but you’d be able to do much, much more than with just the 1200es.
Hi Blue,
First of all thank you very much for this and other posts they’ve been very helpful. We have a uPrint printer and with your help we successfully hacked the machine so we can use Makerbot material instead of the expensive stuff that Stratasys sells. Our printer is running Fedora instead of RedHat and for installing the script we removed the hard drive from the printer and modified the files directly from a virtual machine. If it is any help we can post a more detailed description of what we did.
Since the Makerbot material is a little bit thicker (1.75mm) from the original Stratasys (1.6mm from measurements we did) we are a little concerned about the extra mechanical effort (in the long run) or some overheating that the motor can have. So what we are trying to do now is to change the speed of the model material motor. In the configuration file of the printer there are a lot of parameters but we can find any that may be the speed. There are the PID values for the head motor, but without the behavioral model of the motor I don’t know if it can help us. Well if you are familiar with this file and/or if you want to help us I can send it to you so you can take a look.
P. S.: We have the Maraca EX 3.0 software but really didn’t help, we could only change temperatures, plus the model of our printer is not in the list.
Hey CesarN,
I was wondering if you could post a detailed how to of how you got it to work for you. I saw you responded to Fabiano about what you did but was hoping you could explain it in more newbie friendly terms. Thanks!
Sorry for the english, I use google translator. I’m from Brazil and I have a Uprint, phaco like to know how to use generic cartridges? I have a problem with counting the eeprom. thank you
Hi Fabiano,
I’ll tell you what we did.
First of all we connected with a serial cable to the DIAG port that is in the back of the printer. You can use hiperterminal or any other software like that to make the connection. The parameters are baud 38400, 8 data bits, 1 stop bit, no parity, no flow control. To read the EEPROM you have to type the command:
er 0 0 0 128
For the model material. And:
er 1 0 0 128
For the support material.
This will throws something like this:
Model carrier ID (8 8-bit values)
000000: b3 a6 33 04 d0 14 10 bd ..3…..
Model carrier in bay 0: 128 bytes at address 0 (128 8-bit values)
000000: 06 4b aa e4 cc eb 9c dd f8 01 49 0b 12 ca f7 99 .K……..I…..
000016: 1d 7a bf da a8 dc 68 60 c9 04 12 ac de 6c 4b 29 .z….h`…..lK)
000032: 2e 91 67 93 5f 2a 91 e5 8f 71 6e fe cc 63 79 5c ..g._*…qn..cy\
000048: 8f 71 6e fe cc 63 79 5c bf dd ab d7 c6 22 d5 c6 .qn..cy\…..”..
000064: 22 6b 00 00 00 00 49 f9 55 aa 55 4d 45 01 5e be “k….I.U.UME.^.
000080: 13 de 00 00 00 00 00 00 bf dd ab d7 c6 22 d5 c6 ………….”..
000096: 69 b0 11 90 00 00 00 00 53 54 52 41 54 41 53 59 i…….STRATASY
000112: 53 94 76 71 a1 7d e7 1d 09 22 1d 33 e9 96 d7 f9 S.vq.}…”.3….
Then you have to arrange the data in order to write it to the EEPROM in this format
“06,4b,aa,e4,cc,eb,9c,dd,f8,01,49,0b,12,ca,f7,99,1d,7a,bf,da,a8,dc,68,60,c9,04,12,ac,de,6c,4b,29,2e,91,67,93,5f,2a,91,e5,8f,71,6e,fe,cc,63,79,5c,8f,71,6e,fe,cc,63,79,5c,bf,dd,ab,d7,c6,22,d5,c6,22,6b,00,00,00,00,49,f9,55,aa,55,4d,45,01,5e,be,13,de,00,00,00,00,00,00,bf,dd,ab,d7,c6,22,d5,c6,69,b0,11,90,00,00,00,00,53,54,52,41,54,41,53,59,53,94,76,71,a1,7d,e7,1d,09,22,1d,33,e9,96,d7,f9″
This –> ” “<– are very important.
To write the data you type the next command
ew 0 0 0 "data" For model
ew 1 0 0 "data" For support
Like this:
ew 0 0 0 "06,4b,aa,e4,cc,eb,9c,dd,f8,01,49,0b,12,ca,f7,99,1d,7a,bf,da,a8,dc,68,60,c9,04,12,ac,de,6c,4b,29,2e,91,67,93,5f,2a,91,e5,8f,71,6e,fe,cc,63,79,5c,8f,71,6e,fe,cc,63,79,5c,bf,dd,ab,d7,c6,22,d5,c6,22,6b,00,00,00,00,49,f9,55,aa,55,4d,45,01,5e,be,13,de,00,00,00,00,00,00,bf,dd,ab,d7,c6,22,d5,c6,69,b0,11,90,00,00,00,00,53,54,52,41,54,41,53,59,53,94,76,71,a1,7d,e7,1d,09,22,1d,33,e9,96,d7,f9"
sorry, but do not understand anything, would have an easier way to explain?
hitch when the cable on the machine and the computer, a message on the machine power failure, low battery output. What do you mean?
I connected the cable to the DIAG output and the computer, but not nothing happens, would have to download some program?
My school has a uprint by dimensions printer and I was wondering if this hack would still work for it. It uses p430 cartridges and I was wondering how you would change those
Hello! (and greetings to Milwaukee Makerspace from Pumping Station: One!)
I work at a college in Chicago that happens to have a Dimension sst1200 with an expired service contract… and I’ve been given permission to modify the machine (to reduce the cost of printing for students). Unfortunately, the machine’s firmware has been updated to the latest one, and it seems that there are some differences between your findings and mine.
I’ve got an image of the HD, hexdumps from cartridges at all states (new in box, new in machine, used and not empty, and empty), Maraca 4.0, and a serial connection to the DIAG port on the back of the machine.
I’ve been teaching our old Stratasys technician a few things about the machine as well!
I was hoping I’d be able to pick your brain on some things! Is there any chance I could email you some of the questions I had?
And if you get a chance, tell everyone at Milwaukee Makerspace that TensorFlux says hello! I hope the new space is treating you well 🙂
Cheers!
Hey, greets to the PS:1 crew! We’re not moved into the new space yet (still getting the place prepped), but we’re really stoked about it! On the printer, definitely drop me a line – if you’ve been given permission to hack the machine, I’d love to come down and poke at it myself, as I have no access to any modern Stratasys machines.
any news on recharge chip uprint? Thanks
Nothing yet, but I’m seeing if I can get a few uPrint EEPROMs to look at, as well as trying to find a uPrint to experiment with.
I work with a uprint plus and previously a ST768, and I am very pissed with the toll printing system (I have about 100 spent uprint chips sigh). So pissed I built a tantillus (excellent printer). I wouldn’t be so pissed, if they just charge double or tripple the going rate of ABS, but at times 10 the going rate your having a laugh.
Anyhow I have been in touch with Bolson, and for the last year and a bit, and they have said there material for the uprint is not far away, however that is always what they say. I even offered to buy a chip re-programmer from Bolson with no luck.
So thank-you all for these great comments. I am going to try some of these things over the next few months, fingers crossed there is a way to bulk feed (<1Kg Spool) the uprint!
Hello!
Can anyone explain the exactly hardware and firmware differences between the SST 768 and the Elite? It seems to be identical machines. Would not be possible to “upgrade” a SST 768 to a Elite?
Also, would be possible to use the Insight software to create valid CMB files to be used on the SST 786? The Catalyst are very limited and the SST could do more.
Also interested if the hack can be applied to SST1200es.
jori.makinen(@)gmail.com
Hey guys, I write from Argetina, I have a SST768 and in my country it costs a cartridge around $ 600, so using it is very expensive, I have carefully read the post for reusing the cartridges but it is very difficult for those who have no knowledge electronica. They may do a step by step tutorial to do so?
Thanks for your feedback.
regards
Martin
I forgot, someone has the latest version of CATALYST for my sst768?
Thanks for your feedback.
regards
Martin
Hi,
Has anyone tried to replace the DS chip with a micro-controller, like atmega8?
It’s no problem making a atmega board with a button to reset back to original data.
has anyone been able to connect anything else than the original DS chip to cummunicat with the machine?
Jarno you were asking how to “upgrade” a SST 768 to a Elite.
I have a 768BST, and to me it looks like it’s probably different head since the BST only has one temperature in the head. and the elite probably has two.
Your SST also has two i suspect.
can build with two different temperatures on material and support or can only have one headtemp like on my BST?
I talked to a technician some time back and he said the new one’s are based on ball screws while mine are using wire.
But while ball screws are better at positioning it has nothing to do with what materials it can handle. That is what I’m interested in widening, since i can only use the P400 and breakaway support.
first off i want to be able to use water soluble support, secondly it would be great to be able to use more modern materials.
In my machine it’s ready for connecting another temperature sensor, and probably different two-temp head also. Other than that i suspect it’s only a matter of software?
I will “Root” my BST today and investigate a bit. but don’t be betting on me finding the answer, with two kids and toooooo much work to do, other than hacking.
Anyone done an upgrade from BST to Elite?
Anyone out there with a spare head for an sst or elite mashine?
Hello Peter,
We are buying a SST version, but will be delivered at February. If of interest, I have the 768/Elite Service and Maintenance Manual (713 pages), so you can give a look at it.
About materials, go to take a look on isquared. It is a german company delivering ABSplus and ABS M30 materials for the 768 printers, and it costs 1/3 less compared to original ones.
Would be nice if we could cooperate in this upgrade challange 🙂
Hi Jarno,
I have the Elite version of the printer at my work. is it possible for you to send me the service and maintenance manual ?
I will try to hack it.
hello peter i am based in Argentina, and I have a 768 now that I have to calibrate, it is used machine. Could you share the Maintence Manual with me. We have no manual down here. Also you advice buying the material from inquired or hacking the machine? Thanks.¡ José
Hi Jarno,
i am a teacher and my school have buy a Elite 3d printer, could you send me “the 768/Elite Service and Maintenance Manual (713 pages)”
thanks
vincent
Peter,
I have a SST machine that I’m working on can you send the repair manual. It too old for dealer support.
Thanks,
Mike
It seems to me that we should just be able to source the DS2433 – it’s a commonly available part, and flash the microcontroller with the same (or similar) micro code as on the factory ones. A careful hack might disable the part of the code that decrements/increments the valued stored in the counter.
This means that it won’t be neccessary to bypass the ID code in the chip, provided the user data in the chip is correctly implemented. The trick is figuring out how to decipher the user ID data, compared to the chip code. I see multiple avenues for attack here, since the cartridge chip is easily probed, but it will basically boil down to whether the cryptographic polynomial used for the user hash can be bypassed. It might come down to looking at a de-capped device under a microscope.
May have posted too soon. Closer reading of the data sheet indicates that the ID code is not a user setting like some RFID systems (as I’d expected), but entirely fixed. Soooooo, if that’s the case, then it might be possible to simply overwrite a new chip and do a brain-swap. Anybody want to try?
The DS2433 is not a microcontroller – it’s just a serial EEPROM. The unique serial number of the EEPROM is used as part of the encryption key, so simply copying the contents from one EEPROM to another will not work, as the key is different.
Hi all,
first of all, thanks for the nice docs … I got a BST 768 into my access lately and due to the same motivation to use cheaper or other materials I did open up our machine as well. My colleagues, who were working with the machines did not have the courage to do it 🙂 …
I also did “backups” of all our cartridge chips using a simple 1wire-usb adapter with the basic 1wire demo software, what allows direct reads and writes. I even played around with a simple battery powered microcontroller circuit what would record the chip content (of an unused cartridge) and write back that data when the spool came close to 0% …
Next time when I have spare time, I will move the breadboard circuit to a more professional looking built 🙂 … Probably a TI Launchpad micro kit with USB for approx. $5 could be a good platform as well.
What would be great if those who made experiences with different materials could set up a table with sources, quality evaluation and usage hints, so that others (including me) could more easy gain from those experiences.
So far we have used original Stratasys materials, Bolson and noname chinese ABS, all with good results without changing parameters. To be more productive here, I probably could play around with the MARACA tool, if I could get hold of it, too.
In the moment we are looking for good and cheaper breakaway support material. Any good source in Europe known ?
I’ve a stratasys 400mc.
Based in Central UK.
I’d like to try this modification. I’m looking for a linux consultant to help..Has anyone any recommendations?
Hi all,
I have a SST1200 which does not boot. The Display on the panel remains empty.
I tried Power cycling many times. On the Diag port I got the following:
Running POST
Internal Flash CRC Test [PASS]
SDRAM Addr Test [PASS]
ISA DPM Addr Test [PASS]
Pmd DPM Data Test [PASS]
External Flash CRC Test [PASS]
NVRAM check [PASS]
Supply Voltages
5V supply: 5.07V Range: 4.85 to 5.15 [PASS]
12V supply: 12.00V Range: 11.28 to 12.72 [PASS]
15V supply: 16.00V Range: 13.50 to 16.50 [PASS]
-15V supply: -15.77V Range: -13.50 to -16.50 [PASS]
10V supply: 10.00V Range: 9.84 to 10.16 [PASS]
3.3V supply: 3.30V Range: 3.23 to 3.37 [PASS]
Navigator checksum: 0x12345678
Navigator version: 0x28400F23
Pilot checksum: 0x12345678
Pilot version: 0x34100F20
Pmd DAC Tests
XSin@0.00V: 0.01V Range: -0.06 to 0.06 [PASS]
XSin@2.15V: 2.24V Range: 1.96 to 2.34 [PASS]
XSin@4.30V: 4.35V Range: 3.98 to 4.62 [PASS]
YSin@0.00V: 0.01V Range: -0.06 to 0.06 [PASS]
YSin@2.15V: 2.25V Range: 1.96 to 2.34 [PASS]
YSin@4.30V: 4.33V Range: 3.98 to 4.62 [PASS]
ZSin@0.00V: 0.01V Range: -0.06 to 0.06 [PASS]
ZSin@2.15V: 2.25V Range: 1.96 to 2.34 [PASS]
ZSin@4.30V: 4.34V Range: 3.98 to 4.62 [PASS]
Controller board EEPROM CRC Test [PASS]
Controller Configuration ID: 0
Controller part number: 202414-0001
Controller serial number: 0641-002175
Power Dist board EEPROM CRC Test [PASS]
PDB Configuration ID: 0
PDB part number: 202143-0003
PDB serial number: 0647-001636
CPLD version: 29
ColdFire version: 0 rev: 0
Mariner build: 1710.0
Cause of last reset: Power Cycle
POST successful
last act:289216 / req:244297 / malloc:651/0 / stk:1180/11196
act:279648/268768 / req:234729/231646 / malloc:538/0 / stk:2436/11196
Running POST
Internal Flash CRC Test [PASS]
SDRAM Addr Test [PASS]
ISA DPM Addr Test [PASS]
Pmd DPM Data Test [PASS]
External Flash CRC Test [PASS]
NVRAM check [PASS]
Supply Voltages
5V supply: 5.06V Range: 4.85 to 5.15 [PASS]
12V supply: 12.00V Range: 11.28 to 12.72 [PASS]
15V supply: 15.98V Range: 13.50 to 16.50 [PASS]
-15V supply: -15.74V Range: -13.50 to -16.50 [PASS]
10V supply: 10.00V Range: 9.84 to 10.16 [PASS]
3.3V supply: 3.30V Range: 3.23 to 3.37 [PASS]
Navigator checksum: 0x12345678
Navigator version: 0x28400F23
Pilot checksum: 0x12345678
Pilot version: 0x34100F20
Pmd DAC Tests
XSin@0.00V: 0.01V Range: -0.06 to 0.06 [PASS]
XSin@2.15V: 2.25V Range: 1.96 to 2.34 [PASS]
XSin@4.30V: 4.35V Range: 3.98 to 4.62 [PASS]
YSin@0.00V: 0.01V Range: -0.06 to 0.06 [PASS]
YSin@2.15V: 2.25V Range: 1.96 to 2.34 [PASS]
YSin@4.30V: 4.33V Range: 3.98 to 4.62 [PASS]
ZSin@0.00V: 0.01V Range: -0.06 to 0.06 [PASS]
ZSin@2.15V: 2.25V Range: 1.96 to 2.34 [PASS]
ZSin@4.30V: 4.34V Range: 3.98 to 4.62 [PASS]
Controller board EEPROM CRC Test [PASS]
Controller Configuration ID: 0
Controller part number: 202414-0001
Controller serial number: 0641-002175
Power Dist board EEPROM CRC Test [PASS]
PDB Configuration ID: 0
PDB part number: 202143-0003
PDB serial number: 0647-001636
CPLD version: 29
ColdFire version: 0 rev: 0
Mariner build: 1710.0
Cause of last reset: Power Cycle
POST successful
last act:289136 / req:244217 / malloc:651/0 / stk:1188/11196
act:279648/268768 / req:234729/231646 / malloc:538/0 / stk:2212/11196
Any help would be fine.
Thanks,
Robert
Hi
Have you had any success with this? we have the same problem with ours.
Hi folks,
hope you could help out as our BST 768 stopped to work. I assume there is something wrong with the alignment before starting to build the part.
Whenever were are starting a printout the BST 768 starts to work, the build platform is moving around for some seconds and then the system shows CODE 14,100 on the LCD display and the BST 768 is rebooting.
Unfortunately, the CDROM with the error codes is archived somewhere where we can’t find it. Probably somebody could help us out with the meaning of that error code or
behavior ?
Thanks,
Yogi
HI Folks,
after some search and analysis it turned out that the sensor Z home became defective, but only, when the printer was heating up …
We ordered the switch (a part worth 6€ ) and replaced it and now our BST 768 is running as well as before …
hi I have the same problem with bst 768 and same error CODE 14,100. where is placed that switch and where did you ordered it for €6?
thanks, Filippo
Hi!
I have the error CODE 14,100 with sst768. Could tell us to solve it.
Thanks
You may want to check this forum – there’s some sharp folks there: http://www.3dprintforums.com/forumdisplay.php?f=55
Hi guys!
I have an older BST1200 with recently updated firmware that I’ve been trying to figure out. I’ve written lines into the rc.local to delete any system.dat files I could find among the various partitions but the reloaded/reflashed cartridges don’t seem to be resetting. If I wipe the printers HDD and reload it with my backup.img the reset cartridges can be used so I figure the firmware update must have started storing the EEPROM data in some other files (aside from just in the system.dat files). Any recommendation on how I could go about finding those files?
Best,
Kain
kain3713@gmail.com
other think
I have a problem with a full cartridge. It’s blocked because the tip is inside.
I cut it off and I don’t even see them.
Is there a chance for this cartridge?
Open the cartridge with a 7/64 hex wrench—turn the cartridge upside down, unscrew the four bolts, BUT DON’T OPEN THE CARTRIDGE UNTIL IT’S RIGHTSIDE UP.
Turn the cartridge rightside up, keeping track of the four bolts, cut, loosen, or remove the side id sticker so the top half of the cartridge can be lifted off.
Then you can extend or retract the filament, as needed.
To close it up, make sure the 2 pinch rollers, dessicant bags, and the gasket are in place, then put the lid back on, hold the halves together while you turn the cartridge upside down. Insert and tighten the 4 bolts, and you’re done!
Hi
My friend have a SST 768 and the hard-drive seem to malfunction. Is there any way that he can get the software (OS etc.) to setup another drive ?
Regards
Hello all.
We have a Dimension Elite that we are working over. We successfully installed the rc.local trick to remove the internal cartridge logs, but have been having problems dumping the cartridge chips. We have tried both the arduion approach (1 wire interface etc), and the DIAG port trick. The DIAG report does not echo anything back, and the chips respond with all zeros (including the ROM portion), so it feels like we are doing something wrong on both fronts.
Can someone look over my code snippet and tell me what I am doing wrong? Should I post a link?
Well,
I always used a cheap USB-1WIRE dongle to connect and read/write the chips. BUT, we always are using the DIAG terminal interface as well.
Is the DIAG not answering anymore or just not giving back any EEPROM data ?
I have the exact same problem. I have no idea what im doing wrong.
Hi Meawoppl, may I know how you installed the rc.local trick?
Guys, may be someone of you has Insight software? it should be relatively new, cause i want to experiment with fortus 250mc files.
I’ve done some research and now i am able to print files with 0.07″ layer height with my sst1200es.
I wiдl appreciate any help from you. Thanks. you can find me by mail ashanin @ gmail.com (removes spaces)
Eureka! Nice site. Now, my problem. I have an FDM-3000 which was running fine until I took head out to clean nozzels. Now on startup, the CTM150 user keypad shows that it booted and passed by displaying “Version 2.00 Test OK”, but the FDM controller no longer displays it’s v9.07 check or the controls for the feed motors to LOAD/UNLOAD or any other FDM controller interface. It did a pin-to-pin continuity check of the head-to-controller cable, all good. I tried pressing the RESET button which connects to the DS1232 guard chip, but no “reset” of the FDM controller. I ordered a new HPC46003V20 microprocessor and DS1232 chip, but I read in the data sheets that the microprocessor has built in user programmable ROM in addtion to the two EEPROM’s called “HI” and “LO” mounted on the FDM controller board. I would really like to connect with someone who can troubleshoot an FDM-3000 for cash or sell me the FDM controller service manuals and any BIOS that I need to flash to the microcontroller. It’s a great machine, just some little fiddly component is FUBAR and needs repalcement. Please advise. Thanks.
Also, I wondered if any clever fellow has worked up an Arduino-based controller that can replace the Stratasys controller. That would be a major benefit.
im using a BST120es but somehow i fail to get a serial connection to the diag port.
i tried three different USB2Serial converter, different cables, swapping TX/RX a.s.o.
and all the possible settings for the com-port (38400 8N1) but i never get anything back
from the printer. i used putty (win7), minicom and gtkterm (ubuntu) nothing worked …
does anyone have an idea hint what the problem might be ?!
thnx
Marc
Any chance you can try using a computer with a built-in serial port? I have had mixed results with USB converters in the past, and I run my FDM printers off of computers with built-in ports.
I’m adding this line:
rm system.dat
to etc/rc.local, but it doesn’t seem to be doing the trick. Any pointers would be appreciated.
Jeff
Jeff, newer firmware versions also require /mariner/config/system.dat to be removed. As for the blinking red, you’ll have to see what that’s indicating (it may be normal) – check what colors are defined: http://linux-sxs.org/housekeeping/lscolors.html
Also, I notice that etc/grub.conf is now blinking with a red background in the directory listing. How can this be fixed?
Jeff
Thanks all for all the wonderful information but I am having problems with hacking a dimension 1200. I have followed all the procedures and no go. Has anyone out there simplified the procedure any more? When I try and re-flash the chip it just sits there and does nothing. Any help would be greatly appriciated.
Rick, what are you using to re-flash the EEPROM? Can you do an EEPROM read to see if the contents are what you expect?
hello,
like KELL as saying, someone trying to load code from a full cartridge in a new epprom?
cordially
The best method is to re-write the EEPROM as it was at 100% full – see this post at gnurds.com: http://gnurds.com/index.php/2013/01/02/simplified-3d-printer-hacking/
The newest firmware update I downloaded from the server updates the kernel to 2.6.23.15-137.FC8 from the old 2.4.18-24. Instead of the LILO boot it uses GRUB and loads a disk image at boot.
I guess it’s a nice upgrade but if you opened port 22 before. Updating to this firmware. Closed that hole.
It can certainly be reopened – also, I believe the filesystem is mounted read-only now, so remount r/w before you try making any changes to the firewall settings.
What did you have to download to upgrade the kernel to 2.6.23.15? You later said that 2.6.26.8-57.fc8 wouldn’t work with mariner. Did you find a later version that works with mariner? 2.4.18 is really lame.
Thanks
I mounted the drive in another machine with Ubuntu. chroot’d to the drive from the printer. erased the shadow file from /root/etc/ and then ran passwd root to change the root password. I changed all of the grub.conf files and removed the RO from them.
Best part of this whole thing. Good by Vi. Nano is part of the update.
Yep, mounting the drive in another machine is the easiest way – if you are doing the modifications right on the live system, though, it’s a little trickier with having to remount the filesystem and such.
Just for the fun of it. chkconfig –add sshd will add the sshd to the boot init. chkconfig sshd on turns it on. Then while I was adding port 22 to the iptables I removed the outbound reject rules. Added some DNS name servers to the hosts file. Renamed the hostname to 3D-Printer from Master. Since the printer can now speak to the outside world, I updated yum. And am now in the middle of upgrading the packages from a yum check-update. I think I will either pick up a pata SSD for it. Or possibly a pata/sata adapter and put a more readily available sata ssd in it just because I don’t like old Seagate drives.
Oops. Don’t upgrade the kernel to 2.6.26.8-57.fc8. The mariner modules were not compatible. Grub back to the old one.
Pulled the PC104 board out of my machine to see what it was. Advantech PCM-9371 with 128MB memory. Here is the user manual.
http://advantech.vo.llnwd.net/o35/ProductFile/1-K3BUH/PCM-9371_Manual_ed.1.pdf
Just in case anyone wants to play with the board. It does have a compact flash slot on the back to use a solid state card. IDK why they would put a hard drive in this thing if they could have used that instead.
I’m guessing they skipped using the CF card to make sure that their main drive image was backwards compatible with older hardware (the system software has been very picky about being run from /dev/hdc, for example).
Just for fun. I think I might up the memory in this thing from the 128 to 512 and DD the drive to a CF card. I wonder if I could order something from Advantech with a newer pc on card that would work with this thing. Probably a waste of time. But I just want to mess with it.
I have a Dimension 768 BST and the hard rive is corrupt, completely lost partition 1, if anyone can get me an ISO, discs or clone a drive for me I would be willing to pay for it. I need my machine!!
thanks!
i have a dimension 768 bst, the hard drive has failed. could anyone give me an image of the drive? thanks
noonevav1@gmail.com
sorry email is noonevac1@gmail.com
Matt, I think the drive image may be tied to whatever firmware your mainboard is using, so it may not be a simple re-image job. Also, I’ll mention it in a future blog post, but there’s apparently a new forum for Stratasys users that you might want to ask on: stratasysusers.org
thank you
i have the service manual and went through the trouble shooting. i have squares across all the lcds.
What generation controller bay does your machine have?
how do i tell what generation controller bay i have? if you email me i can send you a picture. my direct email is mattk@flexibleconcepts.com
thanks, any help would be greatly appreciated
Gen 1 electronics have a 186 based controller board, while Gen 2 and 3 have a Coldfire based controller. Gen 3 controller has a column of LEDs on the top right of the board, but Gen 2 does not.
its a gen 1 with the 186. i got a new hd from strat. still have dark squares across all lcd’s. think it might be the SBC which is a Ampro p5v. what goes bad in these the embedded cmos?
turned out to be a bad front display that was keeping the machine from booting and displaying squares across all screens.
I have “Dimension sst1200es” 3D printer. After the voltage source reset suddenly the printer givinig me message “Starting up. Finding home” to lcd display. What should I do? Can anybody help me?
Running POST
Internal Flash CRC Test [PASS]
SDRAM Addr Test [PASS]
ISA DPM Addr Test [PASS]
Pmd DPM Data Test [PASS]
External Flash CRC Test [PASS]
NVRAM check [PASS]
Supply Voltages
5V supply: 5.04V Range: 4.85 to 5.15 [PASS]
12V supply: 11.98V Range: 11.28 to 12.72 [PASS]
15V supply: 15.88V Range: 13.50 to 16.50 [PASS]
-15V supply: -15.82V Range: -13.50 to -16.50 [PASS]
10V supply: 10.00V Range: 9.84 to 10.16 [PASS]
3.3V supply: 3.28V Range: 3.23 to 3.37 [PASS]
Navigator checksum: 0x12345678
Navigator version: 0x28400F23
Pilot checksum: 0x12345678
Pilot version: 0x34100F22
Pmd DAC Tests
XSin@0.00V: 0.01V Range: -0.06 to 0.06 [PASS]
XSin@2.15V: 2.25V Range: 1.96 to 2.34 [PASS]
XSin@4.30V: 4.49V Range: 3.98 to 4.62 [PASS]
YSin@0.00V: 0.01V Range: -0.06 to 0.06 [PASS]
YSin@2.15V: 2.25V Range: 1.96 to 2.34 [PASS]
YSin@4.30V: 4.48V Range: 3.98 to 4.62 [PASS]
ZSin@0.00V: 0.01V Range: -0.06 to 0.06 [PASS]
ZSin@2.15V: 2.25V Range: 1.96 to 2.34 [PASS]
ZSin@4.30V: 4.49V Range: 3.98 to 4.62 [PASS]
Controller board EEPROM CRC Test [PASS]
Controller Configuration ID: 0
Controller part number: 205627-0002
Controller serial number: 0945-000285
Power Dist board EEPROM CRC Test [PASS]
PDB Configuration ID: 0
PDB part number: 202569-0006
PDB serial number: 0948-002057
CPLD version: 33
ColdFire version: 0 rev: 0
Mariner build: 1924.0
Cause of last reset: Software Reset
POST successful
last act:718768 / req:660187 / malloc:849/0 / stk:3240/8792
act:699104/690720 / req:640523/638280 / malloc:760/0 / stk:2724/8792
————————————————————–SS——————————————————————————————–
NMIStatus: 0x0
Flags: 0xc8 : Initialized : MhmReady : ShmReady
PwrControl: 0xd : DC : HeadHeater
Cartridge: 0x3fc3 : ModPresent : SupPresent : ModLoaded : SupLoaded
: ModLatched : SupLatched : ModMatInHead : SupMatInHead
: ReplaceFailed : LoadFailed
XYAxis: 0x0
ZAxis: 0x0
Status: 0x2000
command flag = 0
curve count = -1
modHead = 184 / 0
supHead = 186 / 0
Temps = 89.40/0.00 / 89.40/0.00 / 28.60/0.00
Current Position = 0.00,0.00,0.00
Gantry: GR5K Stage: SR64K
current material: model model fc: 0 support fc: 0
Version: 1924 PLDVersion: 33 Gender: sst1200es
———————————————————————FZ———————————————————————————————-
01/14/14 05:17:24:989: FindZHome.cpp:262:INFO:XY axis not ready:Find Z before Fi
nd Home.
maxts1990@gmail.com
It looks like the ‘XY axis not ready’ error is the issue – can you connect up a cable to the diagnostic port?
yes i can
How to Fix ‘XY axis not ready’ please help me
Okay, I think you’re supposed to use the ‘SS’ command when connected via HyperTerminal, and you should get “X Axis Ready”. If not, use the FH and FZ commands followed by SS. If you still don’t get “X Axis Ready” then your controller board is shot – that’s according to an old photocopy I have. I don’t have any experience with the P-class machines, so I don’t know that I can provide any real guidance. You may want to also ask in one of the threads at gnurds.com or the stratasysusers.org forum.
when entering command “SS” gave the result
NMIStatus: 0x0
Flags: 0x40c8 : Initialized : MhmReady : ShmReady : GlobalsLoaded
PwrControl: 0xd : DC : HeadHeater
Cartridge: 0x3fc3 : ModPresent : SupPresent : ModLoaded : SupLoaded
: ModLatched : SupLatched : ModMatInHead : SupMatInHead
: ReplaceFailed : LoadFailed
XYAxis: 0x0
ZAxis: 0x0
Status: 0x2000
command flag = 0
curve count = -1
modHead = 184 / 0
supHead = 186 / 0
Temps = 100.20/100.00 / 99.90/100.00 / 75.30/75.00
Current Position = 12.50,12.37,-0.00
Gantry: GR5K Stage: SR64K
current material: model model fc: 0 support fc: 0
Version: 1924 PLDVersion: 33 Gender: sst1200es
What does entering “FH” and “FZ” provide?
when entering FH not give a result. but it will start finding home
when entering FZ, XY axis not ready:Find Z before Fi
nd Home.
when entering command “FH” gave the result
INFO:Foam sensor down when it should
be up:Surface sensor down after motion complete
when entering FZ, XY axis not ready:Find Z before Fi
nd Home.
I’m guessing the ‘foam sensor down when it should be up’ may be the issue – is there a sensor that you can check? I have no idea how the sensors might work (I didn’t even know there was a foam sensor), but if it’s a microswitch or an optical flag, check the outputs with a multimeter.
HI,
i have just purchased a BST 768 printer and was wondering if anyone could help
with a a problem I have. when you try to build It shows error 14-21
and shuts down, I have contacted Sys in the UK but have had no reply.
is it possible to obtain a copy of the manual for this machine.
I have a copy of the service manual for the uprint range. but the machines are to
dissimilar for it to be of any use.
14, 21: Abort : Z axis not ready. (PMD chip not ready)
sing the HyperTerminal, type SS. “X Axis Ready” should be displayed.
(Housekeeper needs to be preformed every second but did not)
(Chip that controls the PMD chip not ready)
14, 21: Abort : Z axis not ready. (PMD chip not ready)
If it is not displayed, then type the “FH” & “FZ” commands. Finally type “SS” again. If “X Axis Ready” still is not displayed, then replace the 186/contoller Board.
Could anyone lead me to software for a Stratasys 1650 FDm machine I have.
It did not come with software and can not find anything that would work.
I Get no data on my Dimension SST 768…
it stops at “Sending Eeprom Data”
Could anyone please help me!
i just got that advise that my Printer is to old aged 😉 Any one here who could help? I just dont get any data. Is there a way to get the Data direct from the Chip? I hope anybody could help! Thank you!
reload chip UPRINT?
Hi
I have a SST 1200es. Can some please share any maintenance manual.
Many thanks
Ignacio
I know the thread reference is old, but I’m looking for the service manual for the dimension 768. Any help would be greatly appreciated.
Thanks in advance
Hi all,
i have hacked the encryption ! 😉
the ds-chip-key is not the one the Machine remembers, it is as Serial-Number inside the encrypted block and the chip-key is Part of a bigger Encryption-Key 😉
It is possible to reuse the chip again and again !!!
it would also be very difficult for SSys to keep track of the refilled Chips.
What Do You mean?
Should I Start a Chip-Refill-Service?
Refilling is resistant against Firmware-upgrades 😉
You can test me 🙂
Send me a Chip-Dump with the Chip-Key and wait for a response 😉
You lost me a touch DS_Filler… What is the Chip key, is it not in the Chip Dump in line 3 of your post?
Obviously your not planning on sharing that info… but you are somewhat confusing… what is the DS chip key? the DS serial number?.. what is the encrypted Block?
Ok I’ll send you a Dump.. but what’s the chip key?
Thanks,
Ted
Yes i meant the DS 64-bit serial. Sorry for that confusion
I need the Dump and the DS-Serial to create a new Record you can write back on the DS-chip.
Right now i dont plan to share that info, maybe i will change my opinion in the future?
I dont want to pull down SSys pants 😉 They have to much money and lawyers on their side …
They did a good job in constructing the machine and its internal protection to bind their customers to them.
The De/Encryption uses a key split into
a) a machine-key
b) the chip-serial
c) fixed parts of the Dump
These 3 are brew together and the resulting Block
contains a 64-bit (Material)-Serial-Number you can find in the logs of the Machine when changing the Material 😉
this Mat-Serial and Materialammount is rememberd encrypted in the system.dat ( this behaviour seems to be different in newer firmware as SSys has obviously reacted on the Hack described here )
What i can do with your Dump in connection with the DS-Serial is
a) create a new Mat-Serial
b) Fill to the same or a bigger ammount of Material
c) set any other Material-Type
Greez
😉
Send the Dump to ds_filler(_at_)freenet.de 😉
Or alternatively go here
https://www.google.com/url?q=https%3A%2F%2Fgithub.com%2Fbvanheu%2Fstratasys%2Ftree%2Fstratasys-ng&sa=D&sntz=1&usg=AFQjCNH0R0g5G-TeTZMjvrdcn87wpeUFMA
download the how to and do it yourself, assuming I am understanding things right.
The guy that did it’s homepage I think.
https://github.com/bvanheu
Cool 😉
hi i am unfortunately a new dumb ass that bought a demssions sst 768 off ebay and in up to my ears . i was told “it only needed a print head” but it doesn’t have any words in the lighted display and like i see many of you are requesting help
i have the 4.o catalyst soft ware and a user guide but my computer dont comunicate to or from it(sob/sob more sobs.could ya help a poor helpless dumb ass PLEASE!
im a us vet paying a lot of child support mercy sob sob
Unfortunately, if you bought one that ‘only needed a print head’, it is probably a trade-in unit that had the head, main control board, and hard drive yanked out and sent back to Stratasys. What boards are still installed in the rear? Getting a new head will not be cheap.
Could you send me Service and Maintenance Manual. Please.
Could someone please send me the service manual. The link in the post is no longer working.
I’d Like to add that on my EEPROM dump (P430 cartridge Stratasys Dimension SST1200) 0x4E-0x4F Reads 0x66BE.
Bit late i know, but any byte might help.
So did you actually figure out how to reset the material chip so it can be used again for a Dimension 1200?
We bought a dimension 768 and it works perfect.. but the cartridge issue… we are willing to pay anyone that can walk us through this (may even pay a trip for you to come to denver).. email me at jason dolbin (at) yahoo dot com
I used the diagnostics port to copy the eprom from one fresh cartridge onto an old cartridge. I then rebooted, which deleted /system.dat.
However, the printer now thinks that the cartridge is empty, and the eprom contents have been changed!
Now the display says that it can’t read the cartridge, although I can dump the eprom from the diagnostics port.
I had the same problem and figured out how to solve it. The first time I tried to write the data back to the EEPROM I accidentally copied the entire message, which includes a header with information that you shouldn’t write back to the cartridge. Also try using this tool to format it: http://gnurds.com/index.php/2013/11/14/updated-eeprom-tool/
chelmite, you can’t copy the cartridge contents from one EEPROM to another. The contents of the EEPROM are encrypted in part with the EEPROM’s uniquely lasered serial number. You’ll want to have a look at bvanheu’s program for generating your own EEPROM from scratch: https://github.com/bvanheu/stratasys/tree/stratasys-ng
It may be possible to determine the gender of your machine through the diagnostics port using the rg command. According to the output from my BST1200 the command “displays the current gender as found in the status structure. The gender may be neutral, mariner, dimension, prodigyplus, jib, msi, or schooner. Each of these corresponds to a hardware configuration.”
I would guess that the possible genders is dependent on your model of printer.
Any updates on the Stratasys Material Hack for a 1200es printer?
I have a Stratasys Uprint and want to do this hack but unfortunately it’s over my head. If someone is able to step me through it or even come here to NJ to do it for me I’d be willing to pay. Please contact me at iaknown (@t) hot Mail dot com.
Unfortunately, I don’t think the uPrint can be hacked in this way yet – the problem is that uPrint cartridge EEPROMs use a secret MAC authentication key for writes to be performed.
For Uprint SE, is it possible to wipe out the whole EEPROMs and write back the 100% data?
I believe the uPrint series uses a cartridge with a MAC-protected EEPROM, so this may not be possible at the current time.
I saw a different way of hacking machine. Instead of writing on the EEPROM directly, we can control the machine and ask the machine to overwrite EEPROM. It seems promising.. I would like to know your comment on this
http://gnurds.com/index.php/2013/01/02/simplified-3d-printer-hacking/
Yes, that will work IF the printer’s firmware responds to the ‘er’ command – many people have had difficulty trying to read the EEPROM in that manner. The best method is to use a dedicated EEPROM reader (could be a BusPirate, RasPi, etc.), but for the uPrint SE, you still have the MAC authentication to deal with.
Would anyone happen to know what the root password is on the Dimension 1200es? Does Stratasys use a common password?
I don’t know that there is a proper root password on Stratasys machines – /etc/passwd seems to have non-ASCII characters in the hash for the root password, making it seem implausible that there is an actual password in use.
Hmm, I have some inconsistencies on my hard drive preventing the printer from starting and it is asking me to manually do a repair. But to get to the command prompt to do so it is asking for the root password. The only other option is to reboot which starts me at square one. Any ideas?
If you have a brief LILO boot prompt, you can type ‘linux single’ at the prompt to log into single user mode, then run ‘passwd’ to change the root password. Alternatively, you can mount the drive on a Linux box (or use a live CD) and edit /etc/shadow directly to remove the hashed root password.
I seem to be having trouble dumping the system.dat file. Can someone please walk me though exactly how to delete this file? and/or how to use the rc.local? I am quite new to Linux and can only do a few basic things. I can get as a far loging into root and then I seem to get lost. I tried this command but i dont think it did anything:
rm system.dat
What directory were you in when you did ‘rm system.dat’? Also, do you have a backup of your hard drive? Remember, you’re running as root, which means you can break things in a tremendous hurry (although it was always kinda funny to tell Unix newbs that “rm -rf” was the shortcut for “read mail real fast”). I strongly recommend reading through Dan’s posts at gnurds.com on how to go about the system.dat hack.
Okay, so I went through the gnurds.com post and I’m pretty sure that I did everything correct. But I still get a message from the printer saying that the print cartridge is empty. I saved the original eeprom date and put that back onto the same one that it came from. I beginning to think that the problem is that I let the cartridge go to empty, but I don’t know why that would be a problem if your just writing the code back to full. Can someone please confirm is this is in fact a problem? On the gnurds site it says “You overwrote the near-empty value on the cartridge’s” am I hosed with the ones that I have that are empty?
You made sure to delete /mariner/config/system.dat as well as /system.dat, correct? What do the contents of those files currently show?
Also, what are the contents of the EEPROM right now?
Where can I get a EPROM reader and writer for reading and programing Hewlet Packard ink jet cartridge chips for models 18 and 88.
Unfortunately, I’m not familiar with programming HP inkjet cartridges – however, I’ve heard that the EasyPro 90B is a fantastic programmer for Stratasys EEPROMs – maybe it will work for HP cartridges as well?
Any shot someone could forward me a service manual? Thanks.
Replaced a limit switch in our 768 BST machine and the whole thing went haywire when I turned it back on. The lights and motor power are just flashing over and over…. this stinks.
Might have to try plugging in a screen.
I’ve been using this hack for about a year now without any problems on a BST1200. However the way I’ve been deleting the system.dat file is to remove it as part of the startup routine, meaning that after you flash the cartridge you have to restart the machine. This makes changing cartridges a 10-15 minute affair, and if you don’t have a spare “full” cartridge ready and it runs out during a job you have to restart everything. Was wondering what other people are doing for deleting the system.dat file regularly. Originally me and the guys who were working on it wanted to avoid problems with deleting the file when it might be trying to use it and possibly making the system unstable. But now I think we would like to explore something more useful, like adding a command to the list of options for the diagnostics port or something. We also don’t want to keep a keyboard and monitor plugged in to the printer all of the time.
Just had a look at your blog, and you have some very cool projects and interests! Regarding EEPROM hacking, all current effort has apparently been going into bypassing any modification of the printer itself and instead creating EEPROM images ‘from scratch’. bvanheu on github managed to crack the EEPROM encryption and has created some amazing tools to extract and rebuild the EEPROM information: https://github.com/bvanheu/stratasys
Have a look at this thread for inspiration: http://www.3dprintforums.com/showthread.php?t=1088
Thank you, although I’m afraid I’m woefully behind on updating it with all of my projects. I will definitely try to get that working on a Raspberry Pi, and that thread gave me an idea. I got a friend of mine to make up a quick version of the EEPROM PCB so people can make their own boards instead of having to hunt down used cartridges. The replacement EEPROM from Maxim might not work with the printer (details on the linked page), but it’s worth a shot. I’ve got a writeup and a link to the files on this page: http://chasenachtmann.blogspot.com/2015/01/pcb-for-stratasys-cartridges.html
Cheers
Hi, thank you for this valuable info. I have a Dimension Elite and an older BST 768. I’m keen to give this a try on the BST machine since it is out of life and available for tinkering, but I may need to replace some parts first to get it back online. Which brings me to an issue I hope you may be able to shed some light on. I’m looking for a replacement Single Board Computer for my Elite machine, but the Ampro P5v reached end-of-life in 2007 and the “Littleboard” range is no longer available. Are you perhaps aware of what the latest Elite SBC might be (Stratasys does not release this information)? I’m not sure if Stratasys programs their boards prior to delivery (I’m not a programmer so you guys have the edge on me here), in which case sourcing such an item may be a waste of time. The P5v is IDE and all new SBCs seem to be SATA, but a replacement board from Stratasys is not shipped with a HDD which suggests they keep spares of the P5v SBC (for 7+ years?!?) Thanks in advance!
Try checking Ebay for the old motherboards – I’ve managed to find old ones that way. No programming of the SBC is needed, as it’s just like a PC motherboard – all the ‘programming’ is on the hard drive (make sure you get a hard drive image before you start tinkering!)
Thanks for the tips – and I will certainly image the HDD!
My challenge continues, either to do with BIOS settings or with Stratasys proprietary features on the hardware.
I sourced a 2nd hand P5x Single Board Computer to replace the original P5v, then hooked up a VGA monitor and keyboard.
With the SBC connected to the power supply only, the monitor and keyboard function correctly and I can access the BIOS setup. So that works fine.
Connecting only the Controller Board to the SBC via the PC/104 slot without ANY other cables prevents signal from being sent to/from monitor or k/b.
The machine doesn’t boot when all components are connected as per normal operation, and I’m obliged to flick the switch on the rear to shut down.
If I connect only the IDE HDD to the SBC, the SBC doesn’t recognise the HDD, even if I configure it manually in the BIOS.
So it appears there’s a handshake that’s not being shook. Perhaps the Controller Board checks the HDD before allowing the POST to run? Ring a bell with you? Thanks!
None of this is an issue I’ve heard of before – I’m wondering if the P5x is simply not a suitable substitution for the P5v in a Stratasys machine?
1 too many late nights, and I’d overlooked re-connecting the power cable to the HDD (urgh!). I successfully got the machine running with the X, Y and Z startup dance. All that I need to overcome now is that there is no feed to the display panel. I’m hoping it’s simply a BIOS setting.
Where can i find the maraca software?
tnx
hello, I would like to know if you found a solution to the EPROM for hp 3d. Thank You
Hola tengo una pregunta sobre Display Panel de la impresora Dimensión BST 768-SST 768 ayer estuve instalando el Software Catalyst 4.2,no me reconocía la impresora pero podía interactuar con el Panel de visualización
y hoy el Panel de visualización no es inicia.(no se ve nada)
Alguien podría guiarme.
Nota:
tengo un disk 3.5″ del interior de la impresora (con la inscripción -config disk Pi949)
Muchas Gracias
is it the same thing for a cubex duo
what is the processe for erased all the registred nbr data
No, the CubeX requires using firmware hacks to work around the chipping.
Please can you help me hack “SPIT PULSA 800” GAS NAILER. It uses only original gas ballons and this ballons have RFID chip.
Unfortunately, I don’t have much experience with RFID, but the first thing to do would be to determine what frequency it is using. After that, purchase an RFID reader for the correct frequency range and see if you can read any data…
it is work on HF 13,56mhz, but today i could’t read any data from this rfid tag. I found SWD connector on board of Gun. May be it is possible use this SWD connector to hack and use without RFID.
Can you help me?
Hopefully someone else can assist – my knowledge of RFID is absolutely minimal!
Thank you very much for your answer. But what about reading ROM through SWD connector on the board. It is possible to read flash from chip and then reflash it for disabling counters?
https://goo.gl/photos/i2bSwfxiJ1CSTptK9
Unfortunately, your photo gives a 404 error – could you upload it to imgur?
Thank you very much for your answer. But what about reading ROM through SWD connector on the board. It is possible to read flash from chip and then reflash it for disabling counters?http://imgur.com/dreW22n
Yes, I’m guessing you’re correct in reading/writing through the SWD pads. Can you remove the plastic housing to see the components on the other side of the board?
this board is filled with plastic. And it is not possible to remove housing. May be we can try to scan or research SWD pads? Anyway I will try found this part on eBay for experiments with removing off plastic
Without knowing what the SWD pads actually connect to, it would be very difficult to figure out how to use them – disassembling discarded units would be the best method.
I have a purely software solution to the cartridge issue, which requires no messing with the EEPROM. If someone can send me a hard drive image I will be able to test it and post the results here (I’m still waiting for my 1200es). If someone is interested – barzakov@gmail.com
You can buy the adapter here apparently. http://www.ebay.com/itm/Stratasys-Dimension-Compatible-Ampro-SBC-VGA-Adapter-/181813713072?hash=item2a54f118b0 . It is only for the monitor and you have to send the guy a private message if you want the full Keyboard/Mouse/Monitor/Multi capable adapter. He wanted 249.99 but i got the whole kit for 250. The monitor adapter in the link however is cheap.
this board is filled with plastic. And it is not possible to remove housing. May be we can try to scan or research SWD pads? Anyway I will try found this part on eBay for experiments with removing off plastic.
Please, can send me image hdd disk dimension bst 1200es,
To satelite07@gmail,com, is very urgent! Thank !!!!
Image hdd bst 1200es ? Please
Send to satelite07@gmail,com
Thank
#############################
Thanks for your efforts. I recently got a free 1650 FDM but it only came with the calibration disk and firmware settings (and a whole ton of tips). I don’t want to retrofit if I can help it but the software is extremely elusive. Where did you get Insight 8.1?