Five years ago, I published what is probably the single most popular post on this blog – namely, how to reset a Stratasys material cartridge EEPROM so that it can be refilled with much cheaper third party filament. Dan at gnurds.com took things a step further and came up with some great step-by-step tutorials on […]
Five years ago, I published what is probably the single most popular post on this blog – namely, how to reset a Stratasys material cartridge EEPROM so that it can be refilled with much cheaper third party filament. Dan at gnurds.com took things a step further and came up with some great step-by-step tutorials on how to accomplish this, and even had a post featured in hackaday. I received a lot of questions and feedback on the hack (and even helped hack a few machines running in the field), but the fact that the process requires modifying contents on the printer’s hard drive put it out of reach for users who were barred from doing any sort of ‘invasive surgery’ on the machine (generally students stymied by school officials). What was needed was a truly ‘touchless’ hack that didn’t require any modification of the base machine itself – we needed a way to actually generate our own EEPROM data from scratch rather than simply re-using the EEPROM data as it had come on the cartridge from the factory. The problem is that the EEPROM data is encrypted. Worse, my understanding of how DES crypto is done on a practical level is pretty much zero – I’ve done embedded programming before, but this sort of stuff is far outside my area of expertise.
Fortunately, in 2013 a wizard cracked the EEPROM crypto and posted the code to github! Benjamin’s sorcery is just what’s needed to build your own EEPROM image, and he’s put a great deal of time and effort into it for zero financial gain. As a result, it really bugs me when I see people using his code to sell programmers for hundreds of dollars, with zero attribution for his work. This post, then, shows start-to-finish how you can refill your own P-class Stratasys cartridge using only a Raspberry Pi. It’s admittedly long and detailed, but I think it’s important to understand the whole process before trying to use any shortcuts.
The reason that it’s taken me so long to document this hack is that I previously had no real access to a P-class machine. Fortunately, my friends at Into3D LLC have one in their shop and were more than willing to let me attempt refilling one of their empty cartridges. It’s a Dimension BST 768, which fortunately is still supported for 2 more years. This is what the front panel looks like with a near empty (1% material remaining) model cartridge:
Here’s that very cartridge – the label on top lists some applicable patents (6776602, 7063285, 7341214, D436111, and 7754807):
The side has a recycling information label and identifying information for the cartridge itself – we’ll see how that matches up with the information on the EEPROM itself.
Use a 7/32″ hex wrench to remove the 4 screws on the underside of the cartridge (I used a fold-up set to break them free first, then a standard L-wrench to remove them).
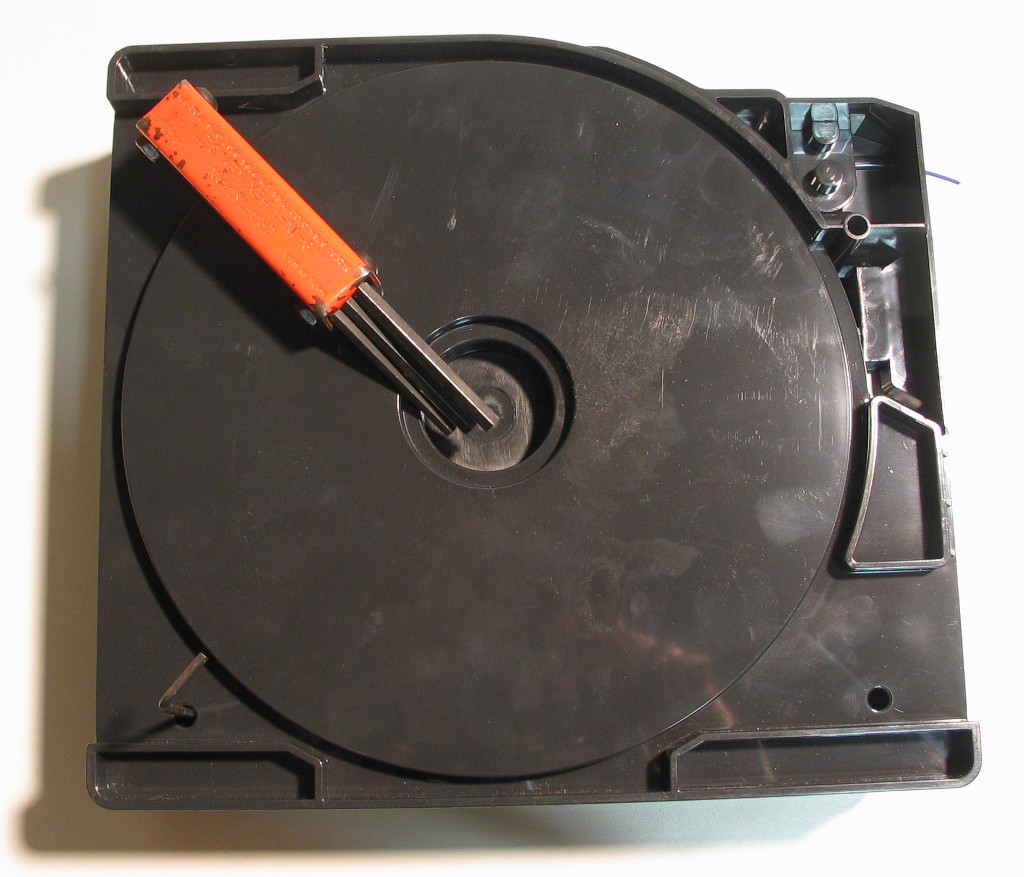
Then, flip the cartridge over and give the shell a few raps with your knuckles to shift the internal desiccant packs into the bottom half. Carefully lift off the top half of the cartridge, exposing the 1% of material remaining on the spool:
Despite my dislike of using cartridges for 3D printers (it’s a lot of excess material to house the consumable), these are actually quite well designed – there’s a pair of very simple drive wheels at the corner exit, and the other 3 corners get desiccant packs. The orange-brown circumferential seal has a spot for the filament to exit through, and the screws actually thread into brass inserts, not into the raw plastic. A single cartridge can be reused many times, potentially lasting a fair portion of the life of the actual machine. Parked right next to the drive wheels in a slot is the object of our interest, the EEPROM board itself:
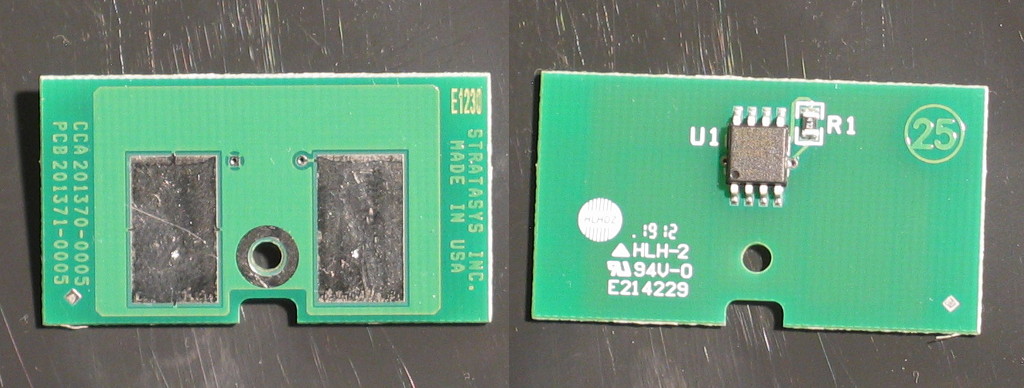
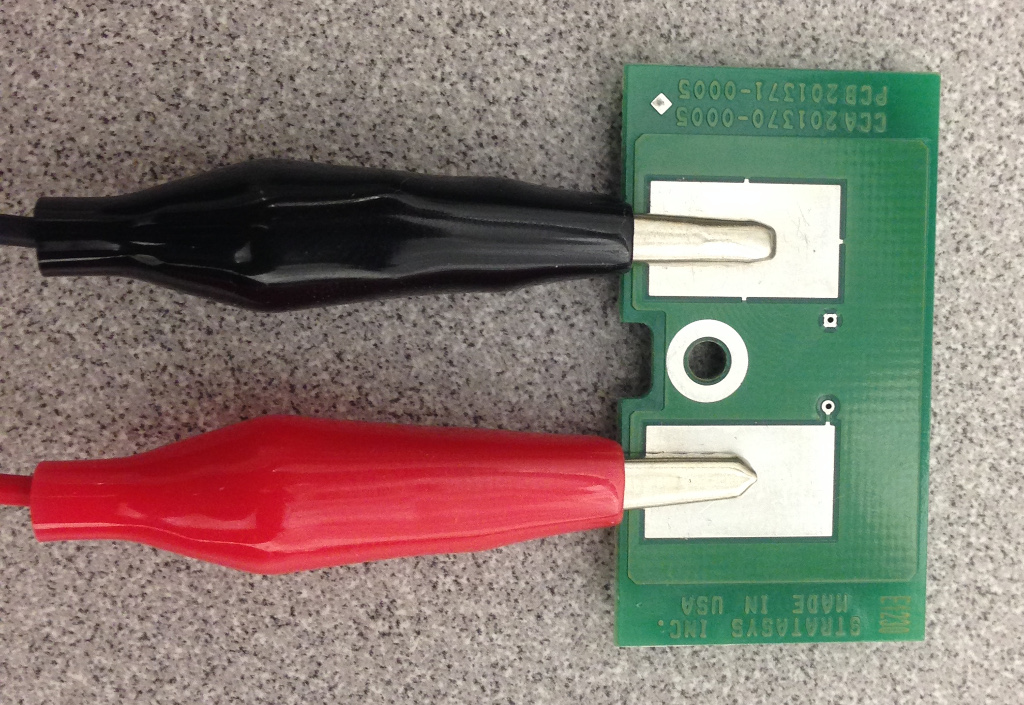
Here’s what the front and back of the EEPROM PCB looks like:
In case anyone is wondering, the text on the chip itself is:
DS2433 1226B1 586AC
As noted in the original blog post, the chip is a DS2433 (originally a Dallas Semiconductor product, hence the ‘DS’, now owned by Maxim). Importantly, it is a 1-wire device, hence requiring only 2 contacts to the chip. As an aside, this nomenclature has always annoyed me – power and signal may be carried over a single wire, but you still need a ground connection.
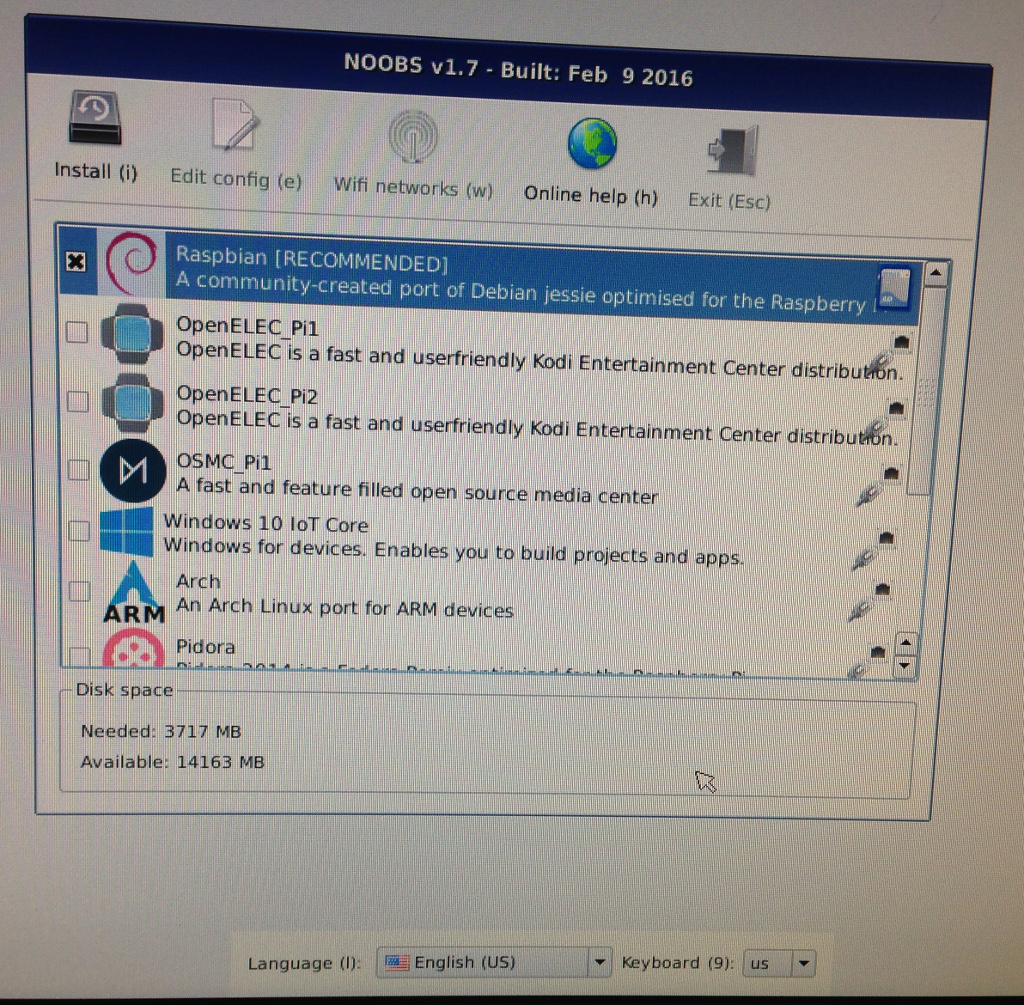
Now, to extract those pesky bits from the EEPROM, all 4096 of them! Technically, there’s a few more bits that we’ll need as well – a 48-bit serial number, 8 bits for CRC, and an 8-bit family code (0x23). I’ve used a Bus Pirate before, and you can use an Arduino as well, but for this post I’ll be showing how to use a Raspberry Pi, since we can do everything on a single, standardized platform. In this case, I’m using a Raspberry Pi model B with an Adafruit breakout board, and I started with a clean NOOBS image (v1.7.0 to be specific) on a freshly formatted SD card.
I booted the RasPi and was greeted with the installer – since I had the RasPi connected to my network, it provided me with network installation options, but I selected only the first option to install the Raspbian OS:
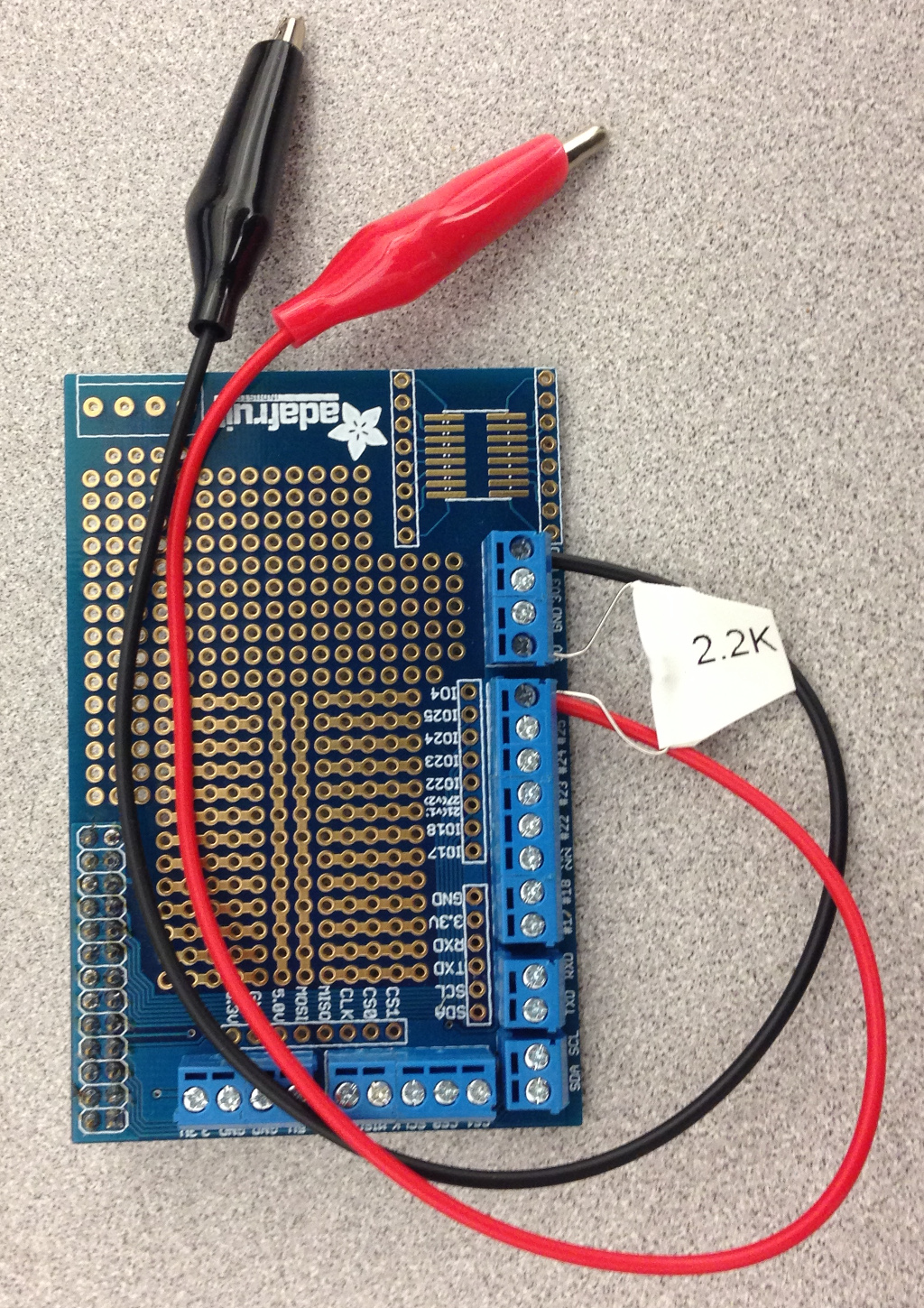
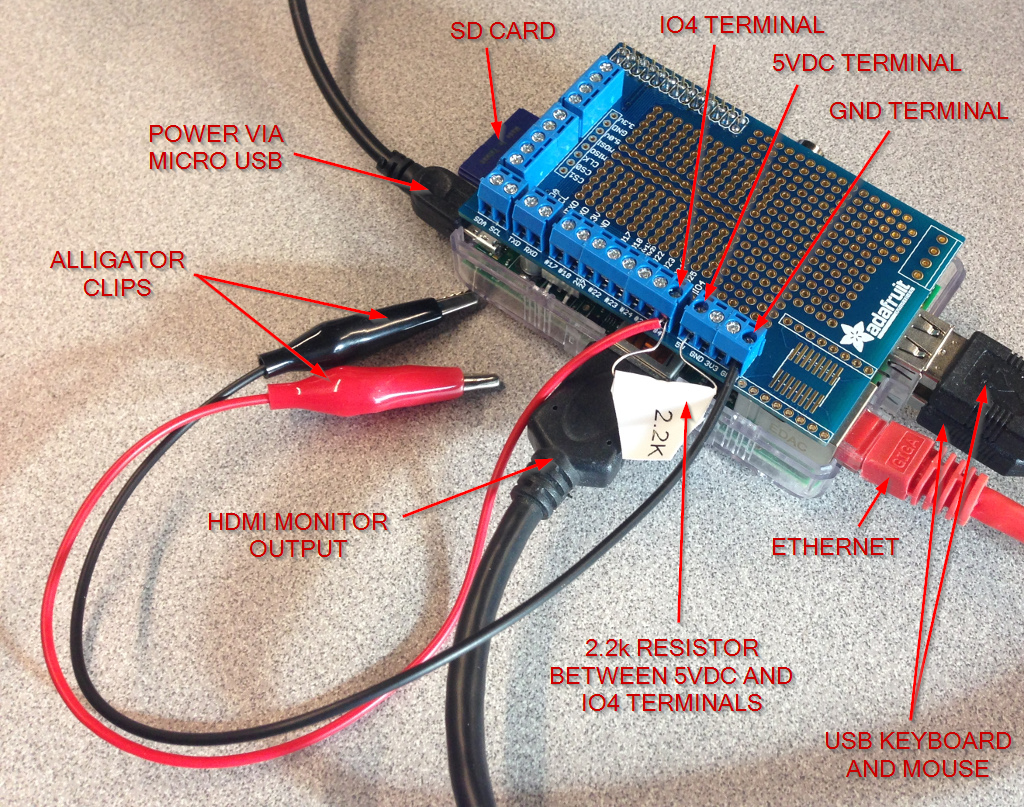
While that was installing, I prepped the breakout board.
I connected the black alligator clip to a GND (0vdc) terminal and the red alligator clip to IO4 on the breakout board (which is pin 7 of the RasPi header). Note that pinouts on the RasPi can be very confusing – IO4 on the breakout board is not GPIO.4 on the RasPi as I had first thought, but pin 4 of the Broadcom BCM2835 processor at the heart of of the RasPi (also known as GPIO.7 on the RasPi). You can read more about this confusion at wiringpi.com. I connected a 2.2k resistor to a 5vdc terminal and the IO4 terminal – this acts as a pullup.
By this time, Raspbian had finished installing and I was looking at a fresh new desktop. I find it easier to just SSH into the RasPi, so once I determined its IP address (just hover your mouse over the network icon in the upper right of the desktop), I could fire up PuTTY and connect right to a shell (you can certainly do everything via a terminal window on the desktop, though).
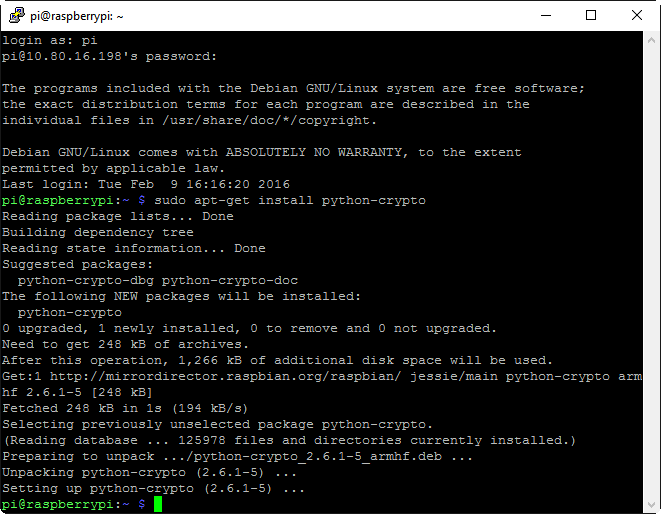
On a default install of Raspbian, the login is pi and the password is raspberry. While Raspbian includes just about all the software we’ll need by default, the Python crypto library will be required later on, so run sudo apt-get install python-crypto right away to install that package (the RasPi will need to be network connected with internet access for this to work). I then attached the breakout board to the RasPi and proceeded to do some testing with gpio to make sure that my wiring was correct.
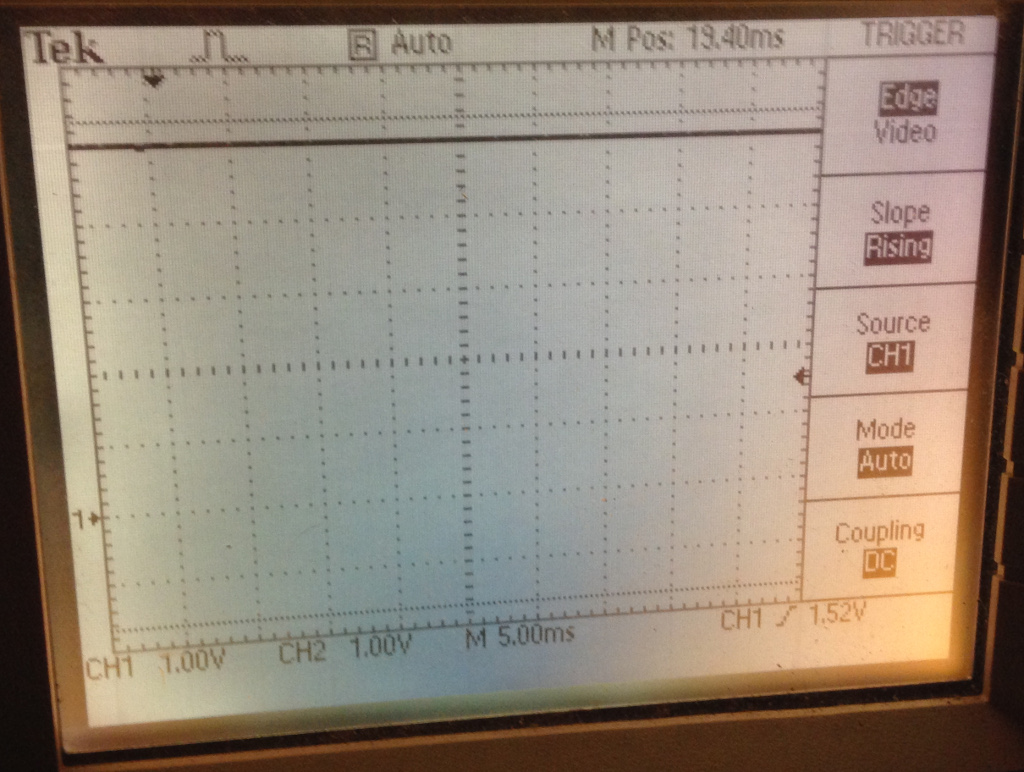
I hooked up an oscilloscope to the red and black leads (you can use a multimeter, but a scope will let us see when EEPROM reads are occurring, which is handy when debugging), and saw that I had nearly 5vdc, which is just what I was expecting due to the 2.2k pullup resistor.
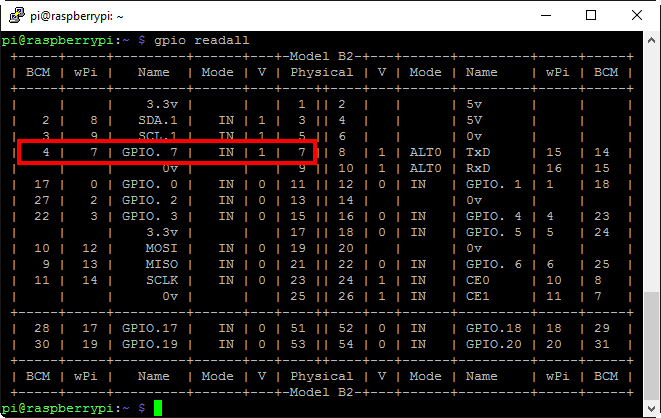
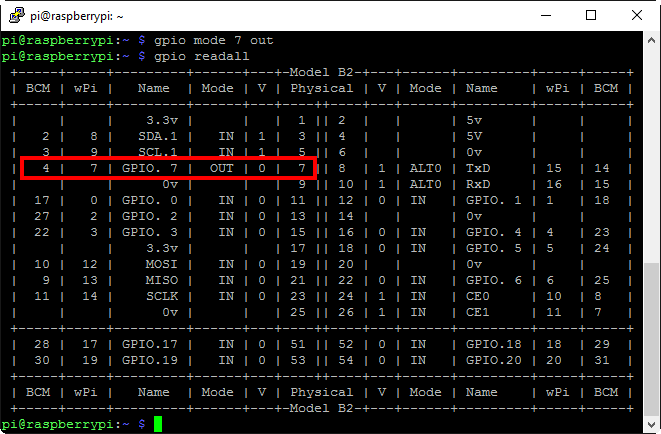
Now, let’s have a look at actually controlling the pin that the red alligator clip is connected to. The gpio readall command gives us a snapshot of what the status is of all the header pins (again, see wiringpi.com for details). By default, all the I/O pins are set to be inputs (note pin 7 is set as ‘IN’):
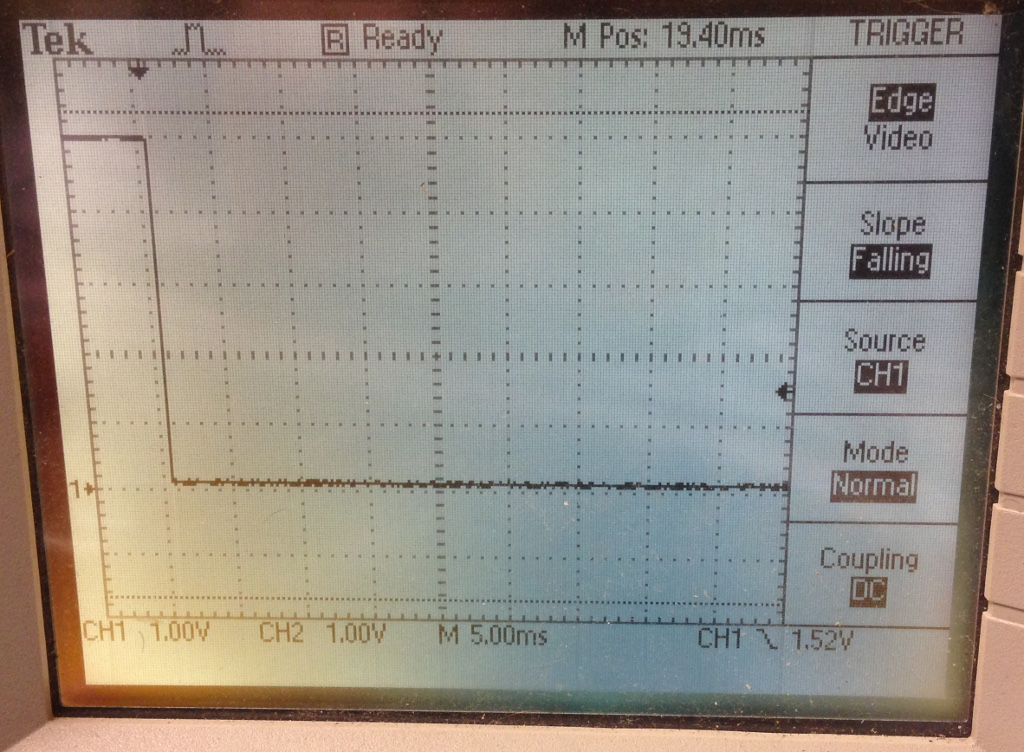
We can change the mode from input to output on that pin with gpio mode 7 out
And as soon as that command is issued, the voltage drops to zero:
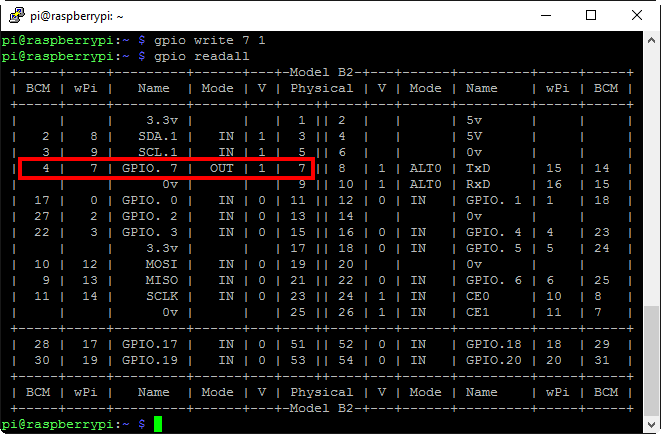
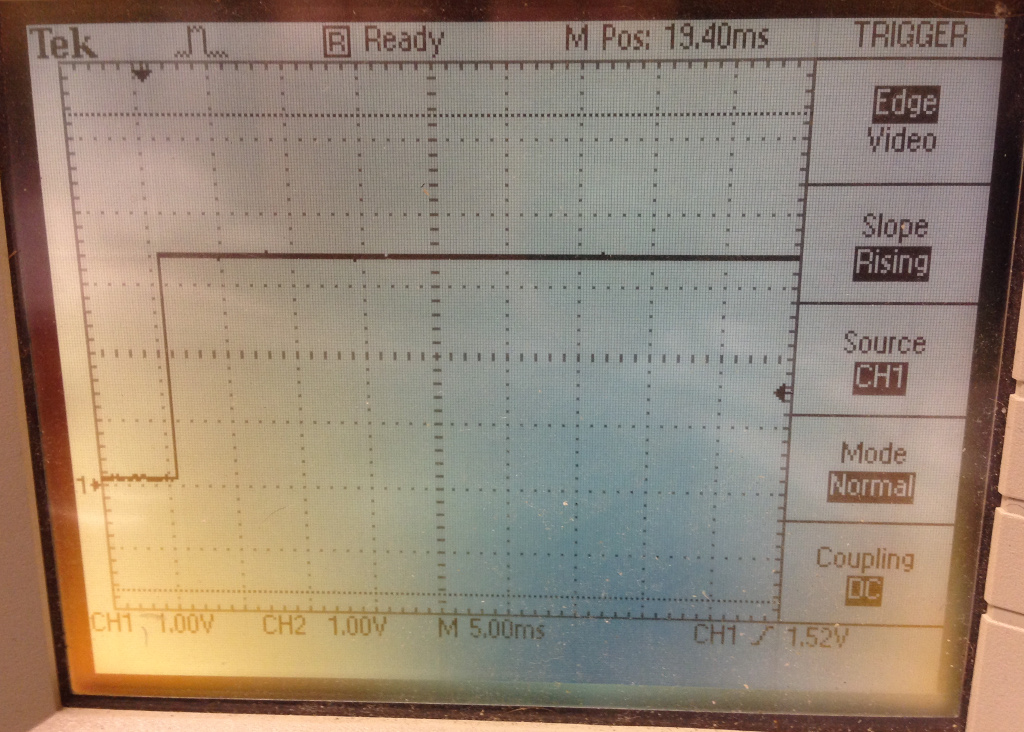
Issuing gpio write 7 1 will bring that pin high:
Resulting in 3.3v output (RasPi digital I/O is 3.3v, not 5v):
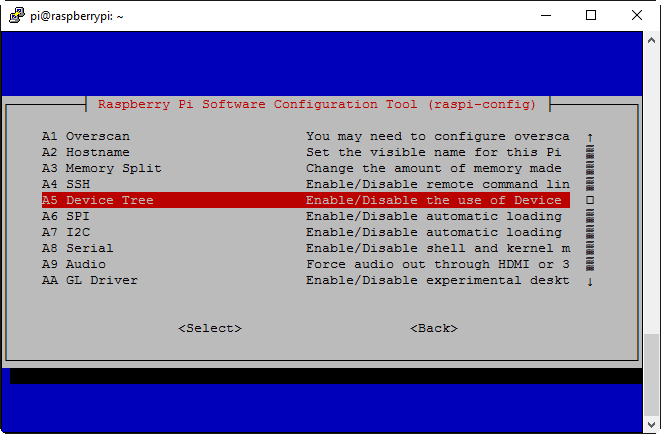
That’s all for verifying that the wiring is correct. There’s one final change to make before we can actually try reading in an EEPROM, and that’s disabling Device Tree (I understand it’s possible to get things working with DT enabled by means of some other configuration changes, but disabling it altogether is the route I went with). Run sudo raspi-config to bring up the configuration menu, and select Advanced Options:
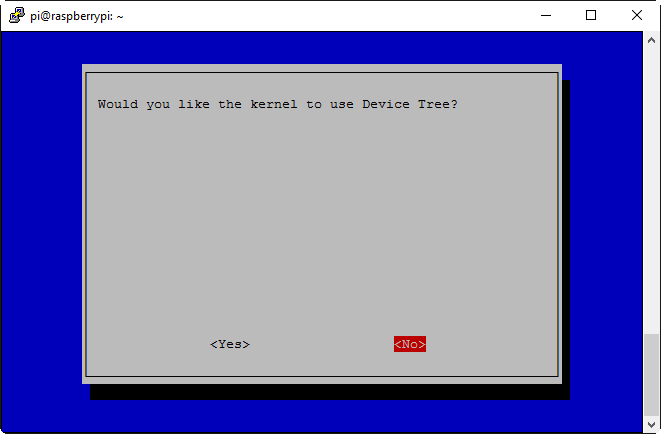
Then, select Device Tree:
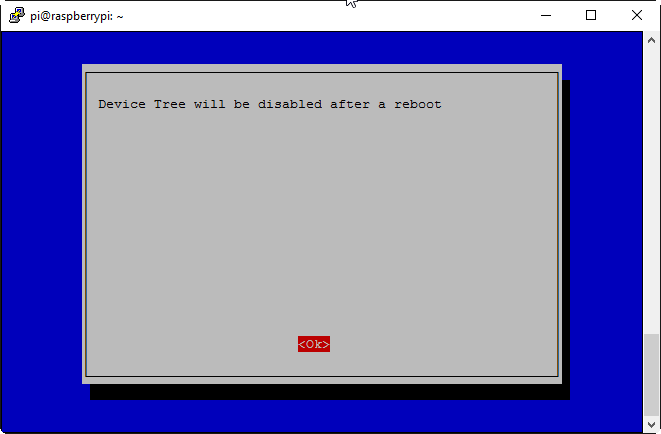
Select ‘No’:
And DT will then be set as disabled:
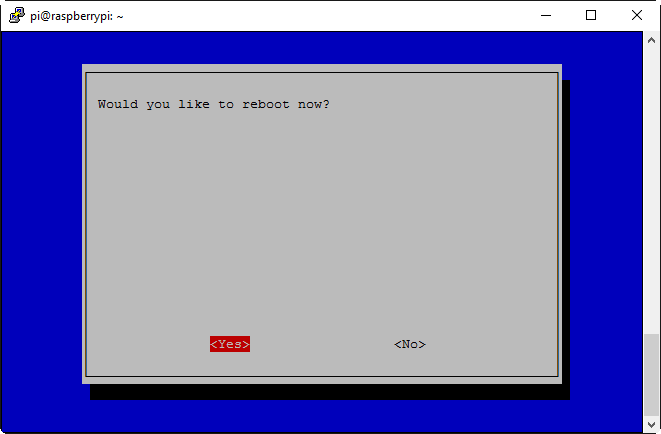
Back at the main menu, select Finish and you’ll be prompted to reboot (select ‘Yes’):
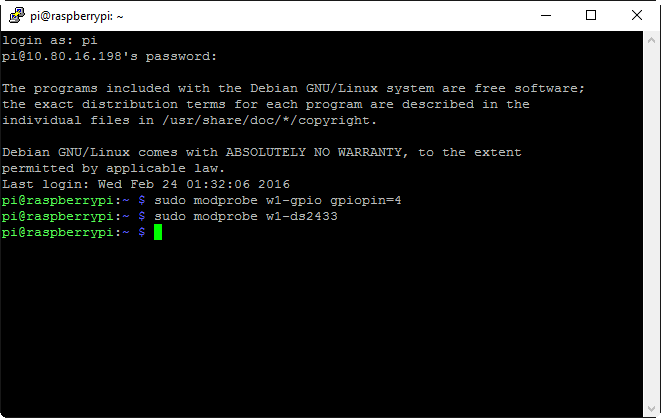
With the RasPi rebooted, we’re finally ready to read in an EEPROM. Recite the magic incantations sudo modprobe w1-gpio gpiopin=4 and sudo modprobe w1-ds2433 (note that you’ll need to run those commands again if you reboot the RasPi, so it may be worthwhile to add them to a startup script):
Now, connect the clips to the EEPROM – black clip to the ground pad, red clip to the data pad (you can tell which is the ground pad because it has a trace on all 4 sides connecting it to the ground plane):
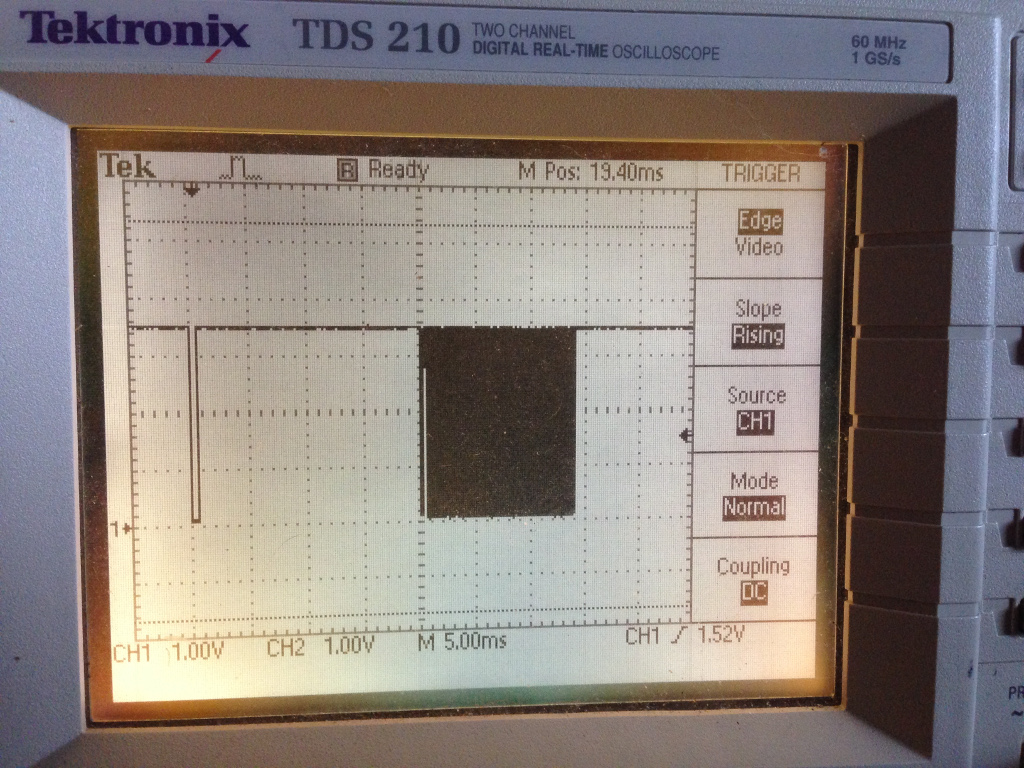
If you have a scope hooked up, you’ll see that the voltage drops to 3.3 volts and then there will be a data read every 10 seconds or so:
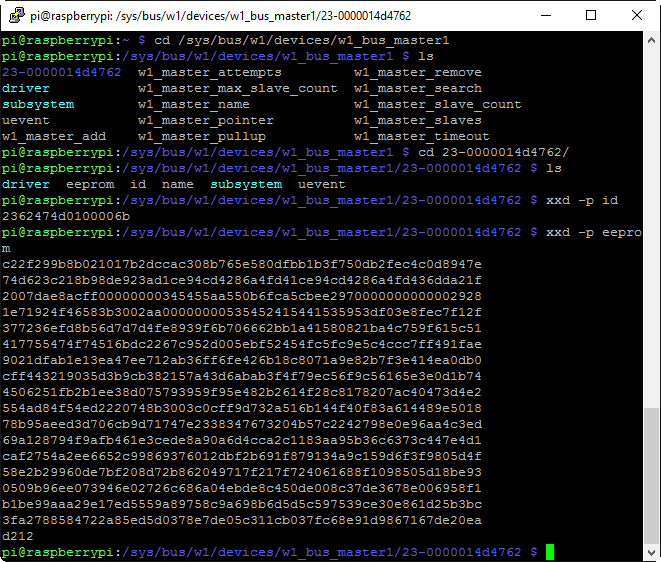
We can cd /sys/bus/w1/devices/w1_busmaster1 to have a look at the connected 1-wire devices seen by the RasPi, and therein is a specific directory created for that EEPROM (23-0000014d4762 in this case – your EEPROM will be different!):
You can also use the xxd command to hex dump the EEPROM’s full UID as shown (0x2362474d0100006b). This particular UID consists of the family code (0x23, which should be the same on all Stratasys P-class EEPROMs, except for those used on uPrint cartridges), the device serial number (0x62474d010000 – note the endianness) and finally the checksum (0x6b). The screenshot also shows a dump of the 512 bytes of EEPROM data itself. In order to actually do anything with this EEPROM data, though, we’ll need Benjamin’s code.
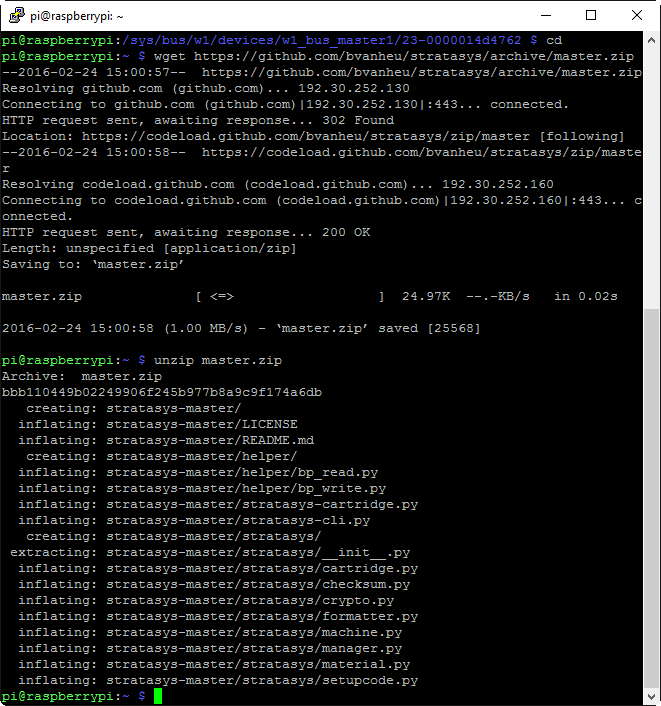
We’ll cd back to our user directory and then grab a .zip archive of the code via wget https://github.com/bvanheu/stratasys/archive/master.zip, after which we can extract it into a directory via unzip master.zip.
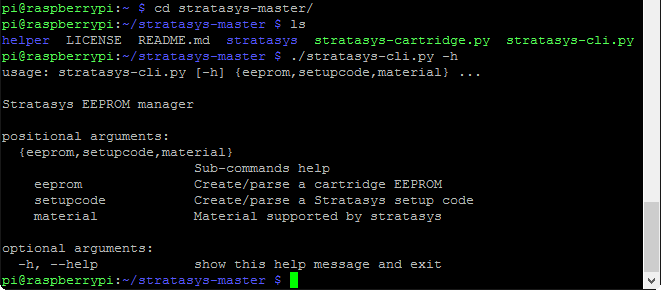
We’ll cd into that directory and try running the main program by executing ./stratasys-cli.py -h
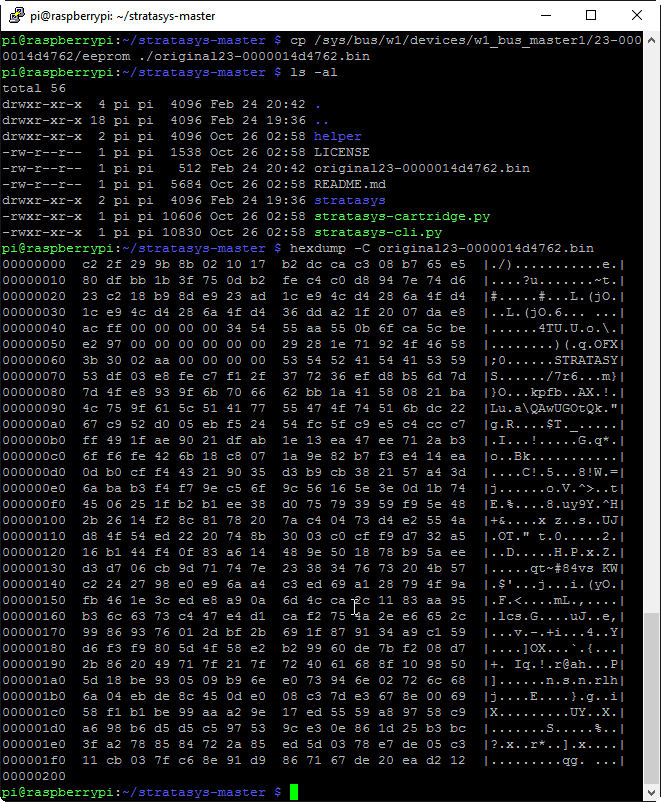
This is just what we want to see! If instead you get a number of errors mentioning crypto, make sure that you have the python-crypto library installed. At this point, we don’t need to do any further configuration on the RasPi, and we can actually dive into the EEPROM data itself. If you’ve managed to get this far, you’re probably capable of basic command line Linux work, so I’m going to gloss over those details from this point onward and let screenshots do most of the talking. First, we’ll copy the EEPROM data out to a file that we can actually work with.
A directory listing confirmed that the resulting file is exactly 512 bytes in length, and all the formatting looks just like all the other Stratasys EEPROM dumps I’ve seen. Let’s take one more look at the EEPROM UID, as we’ll need to format it correctly to feed into the stratasys-cli program:
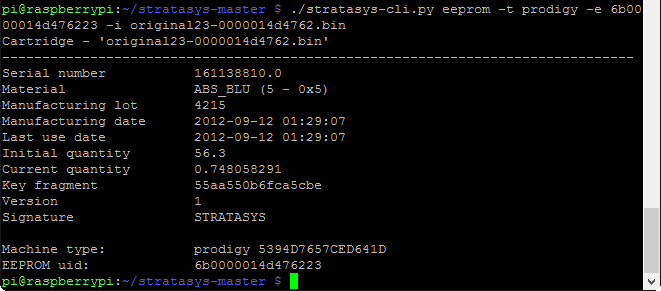
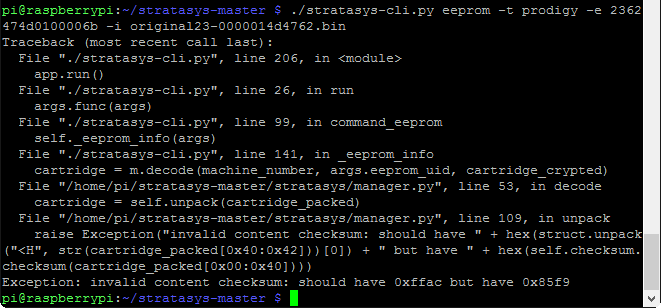
We need to reverse the byte order of the shown UID, so instead of 23 62 47 4d 01 00 00 6b we’ll use 6b 00 00 01 4d 47 62 23 (remember, the family code of 0x23 is at one end, and the checksum is at the other end). Here we finally feed the EEPROM UID and the EEPROM data through the program, using ‘prodigy’ as the machine type (any Dimension series machine should be ‘prodigy’, but a different machine type (Titan, Maxum, etc.) will have a different family name):
If you don’t have the UID formatted properly, the program will fail with a checksum error:
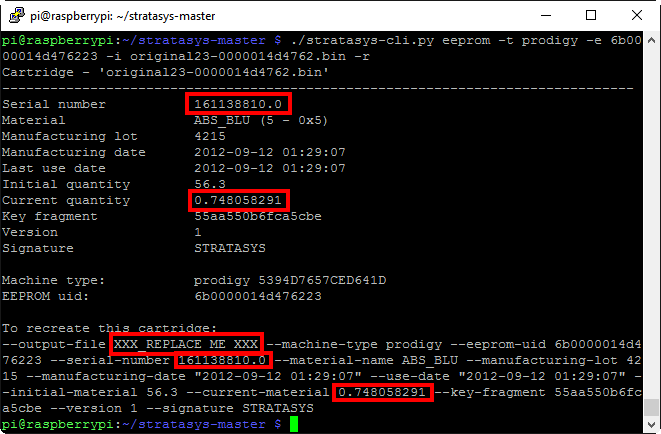
If we take a quick look at the data, everything agrees with the label that was on the cartridge – the color, serial number, manufacturing lot, and manufacturing date all match perfectly (I’m guessing that the timestamp on the EEPROM data is actually GMT). Note that while the last use date is a separate entry in the EEPROM data, I’ve never seen it differ from the manufacturing date (maybe Stratasys intended to write this data back to the cartridge, but couldn’t be certain that the printer itself would actually have the correct day/time set). A service manual I saw indicated that this timestamp was intended to be the date/time that the cartridge was actually first inserted into a machine, so perhaps Stratasys intended to have cartridges ‘expire’ after a certain amount of time.
The EEPROM stores material quantity in terms of cubic inches. A brand new cartridge contains 56.3 cubic inches worth of filament, and the current level as shown on the EEPROM is under 0.75 cubic inches, so the 1% filament remaining message on the printer’s front panel was right on (there was actually a little more than that remaining on the reel, but the overage allows for nozzle purges, waste due to swapping cartridges, etc.). The original hack worked by simply setting the current material quantity back to 56.3, but the printer would remember the serial number of the cartridge (and refuse to work with that cartridge serial again), so files needed to be deleted on the printer itself. Since we can now create our own EEPROM images from scratch, we can simply change the serial number in addition to the material quantity, and the printer will be none the wiser.
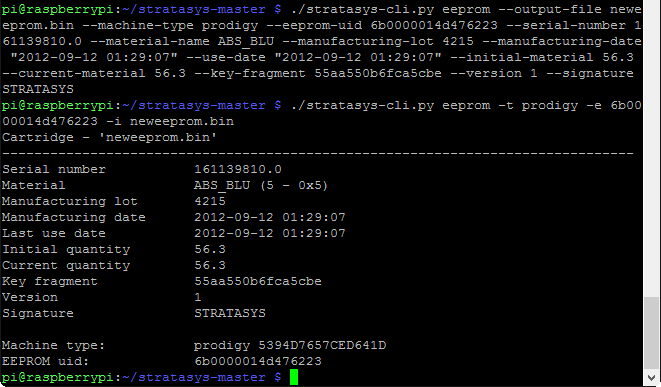
In addition to decrypting the EEPROM data and displaying it in a human readable format, Benjamin’s program can provide all the parameters needed to generate that very EEPROM data, which is extremely handy. We’ll simply tack on the -r option to the command we just used:
We only need to change the highlighted options to create our desired EEPROM image:
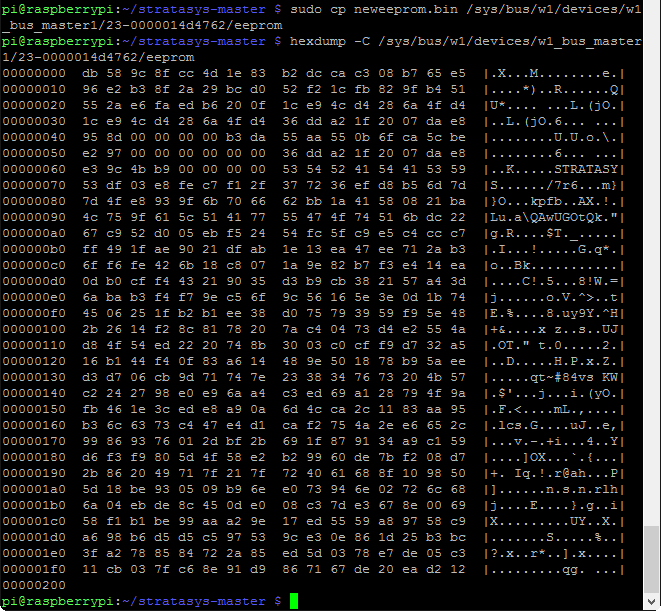
Reading the generated neweeprom.bin file back through the program shows that the serial number is now different (I incremented the value by 1000 rather than 1 just in case there were consecutively serialized cartridges the machine had already seen), and the material quantity is back to ‘full’. Now, we can finally write that file back to the EEPROM itself (remember to use sudo when writing to the EEPROM due to permissions):
A quick hexdump directly from the EEPROM verifies that we’ve modified the contents successfully. Note that the new image we generated is only 113 bytes, while the original EEPROM data is a full 512 bytes. This is because everything after the ‘STRATASYS’ at 0x69 is random garbage (early on, Stratasys simply padded out 0x71 onwards with zeros), so that portion of the EEPROM can be left unchanged. That’s all that we need to do with the RasPi – the EEPROM can be disconnected and set aside. All that remains is to reload the cartridge with fresh material.
My favorite current filament is the ‘High Performance ABS’ from Coex3D – I’m partial to them because they’re local, their product quality is excellent, and Chris gave an amazing presentation on polymer processing and filament extrusion to our 3D printing user group a few years ago. He listened to my pleas for MG94 filament and thankfully started producing it.
While Coex3D reels fit right into my FDM series machines, they don’t fit into P-class cartridges (the bore is just a little too small, and there is a rubber piece attached to the top shell of the cartridge that would interfere anyhow). So I needed to respool the new filament onto the old reel.
In fact, respooling the filament itself is probably the hardest part of the entire process! I admittedly got a bit hackish with the use of electrical tape as a makeshift drive dog, but it worked.
Make sure that you have the desiccant packets in place, the EEPROM PCB in its slot, and the drive wheels in position, then very carefully feed the end of the filament through the hole in the disc portion of the gasket. Hold the filament in its guide slot, and carefully place the top shell half back in place (this is pretty tricky without having the gasket jump out of place). Flip it over, assemble the cartridge with the 4 screws, and our work is complete. Now, for the moment of truth…
After loading the refilled cartridge into the printer, it showed a 100% full model spool!
Of course, the proof is in the prints, and the machine is now happily churning out parts far more inexpensively than before (and with better material properties than the OEM P400 filament had).
Notes:
1) Benjamin’s code works for other Stratasys printer families as well, including the big T-class and Maxum/Quantum machines. It will even decrypt and generate binary images for uPrint cartridge EEPROMs. However, uPrint cartridges use a different EEPROM model that unfortunately utilizes an HMAC authentication scheme for writes. So while you can read EEPROMs and generate new .bin files, actually writing them back to the EEPROM is impossible without knowledge of the secret key used for the HMAC authentication. If you only have access to a uPrint, you’re kind of stuck. [12FEB2017 addendum] It turns out that an HMAC protected EEPROM can be re-written by using the DIAG port on the printer. ‘Odin’ discovered this workaround and authored these concise instructions for the hack. This isn’t quite ‘touchless’, but until someone breaks or sidesteps the HMAC protection, it’s the best option.
2) 56.3 cubic inches isn’t actually the maximum material quantity you can set on the EEPROM. It’s a floating point number, so the sky is the limit! However, on a P-class machine, 60.0 cubic inches is the maximum that the printer will accept as valid, as anything larger will instead be considered zero. [22FEB2017 addendum] Reports indicate that larger volumes can be used, but the ‘initial material quantity’ field needs to be similarly large. However, others (Odin, for one) find that this doesn’t work on their machine, so this could be a difference between firmware revisions.
3) I mentioned using an Arduino to read/write the EEPROM. There’s actually a fork of Benjamin’s code available on github called CartridgeWriter that runs in Windows and interfaces with an Arduino for EEPROM reads/writes. I haven’t tried it myself, but others have used it successfully. I prefer running Benjamin’s code directly on a RasPi due to the amount of control it provides. Specifically, it makes some automation possible, such as…
4) …this clever little EEPROM rewriter made by Sneaks Hacks. He’s posted the wiring schematic and STL files for the housing, and is currently working on an updated version as well as documentation for people wanting to build their own.
5) The Stratasys EEPROM PCB has a surface mount 4.7k pulldown resistor right next to the DS2433. While most wiring schematics for reading/writing a Stratasys EEPROM show to use a 4.7k pullup between 5v and the data pad, I used a 2.2k to help ensure that voltage to the DS2433 remains in an acceptable range. You can certainly start with a 4.7k pullup and reduce the resistance if you’re having flaky results, but I don’t think I’d go below 2.2k.
6) Benjamin notes that use of the –output-file option when generating EEPROM images isn’t actually correct in a traditional Unix sense, and that I/O redirection is really the proper Unix way to get binary output from stratasys-cli.py (that is, using something like ./stratasys-cli.py –foo –bar > my_file.bin). I think using –output-file is a little easier to see and understand what’s going on, but if you’re building an automated system like Sneaks Hacks did, using stdout can help streamline the processing chain. For example, you could write directly to the EEPROM and save a backup of the image all in one go by using something like ./stratasys-cli.py –foo –bar | tee backup_image.bin /sys/bus/w1/devices/w1_bus_master1/23-0000014d4762/eeprom.
7) Everything in this post is simply the compilation and distillation of other people’s hard work – I simply wanted to bring it to a wider audience. These are the folks who deserve all the credit:
- Huge thanks goes to Mjolinor, who I believe was the first to pioneer using a RasPi as an all-in-one solution for rewriting Stratasys EEPROMs.
- Thanks to the anonymous and unnamed people (you know who you are) who have assisted in developing and testing these techniques over the past few years and helped review this post before publishing.
- Steve, Joe, and John at Into3D LLC for letting me use their Dimension BST 768 as the guinea pig for this project.
- First, last, again, and finally, Benjamin Vanheuverzwijn. This man is an absolute electronic wizard and none of this would have been possible without him. Send him coffee.